Configure Threat Exchange Business Rules - Netskope Knowledge Portal
Por um escritor misterioso
Last updated 15 maio 2024

Free eBook: Detecting Insider Threats & Attacks For Dummies - Channel IT

Videos KuppingerCole
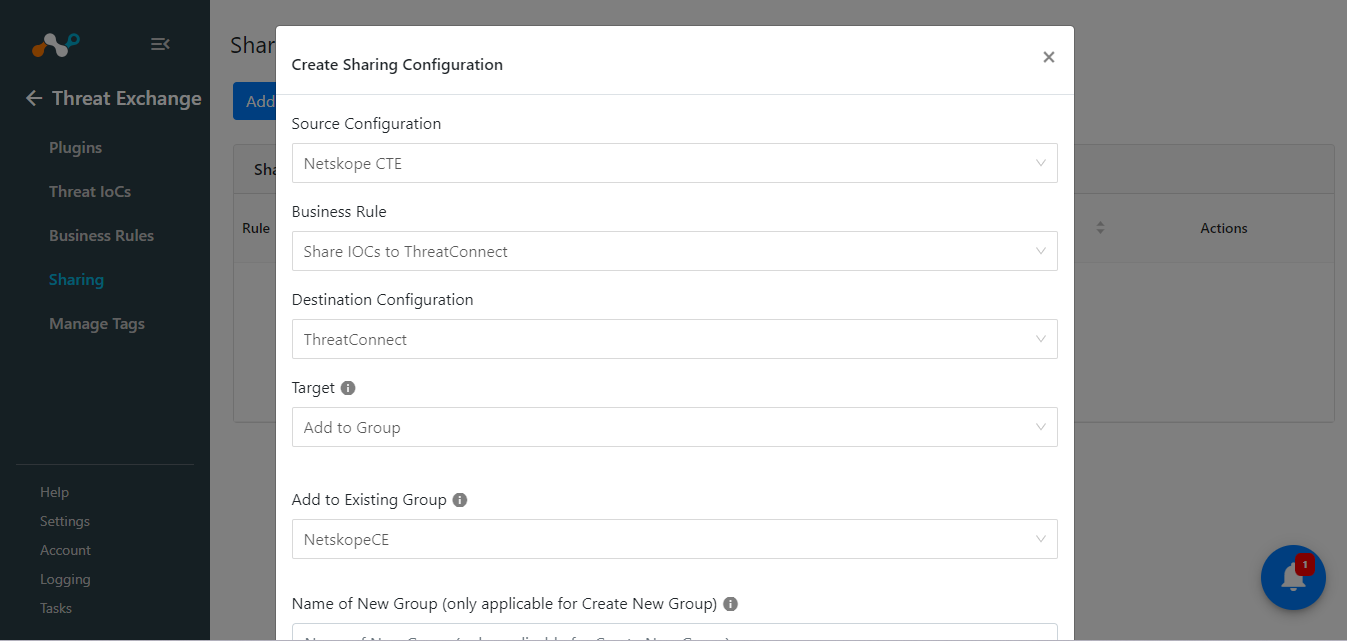
ThreatConnect Plugin for Threat Exchange - Netskope Knowledge Portal
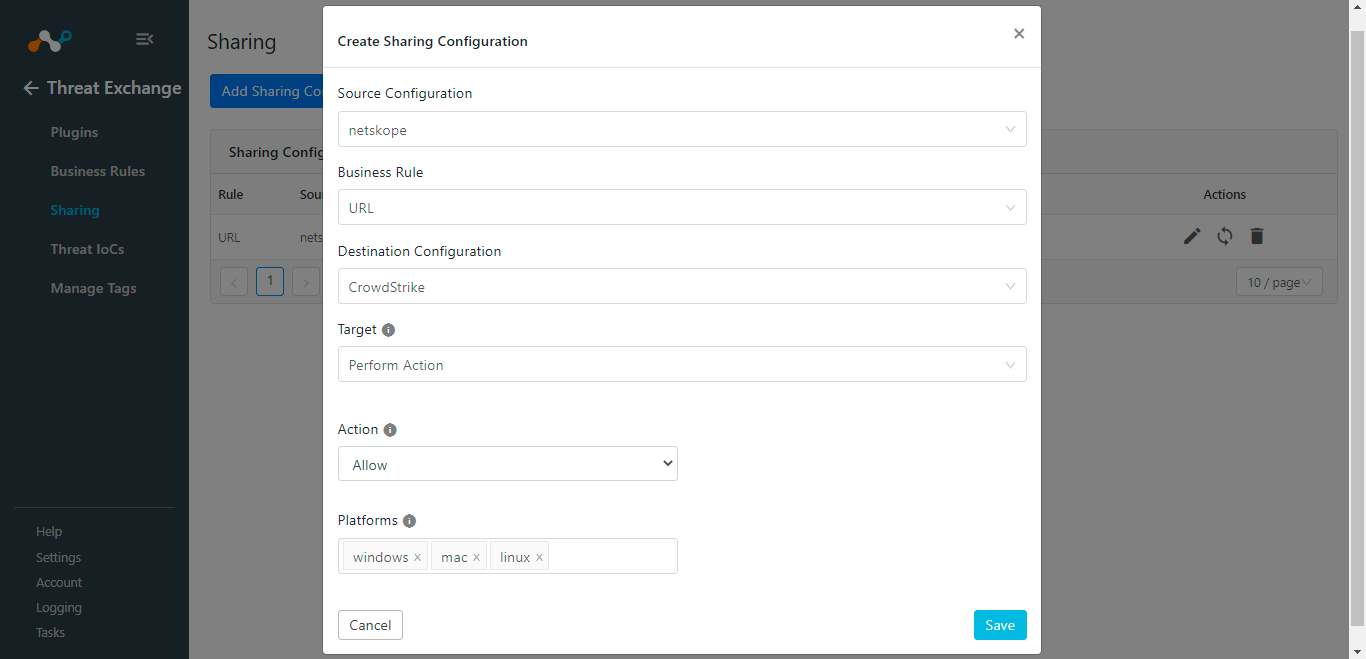
Map a Threat Exchange Business Rule to a Target - Netskope Knowledge Portal
Secure Portal single sign-on configuration

Business Chief APAC - December 2020 by Business Review Asia - Issuu

The Anomali Blog
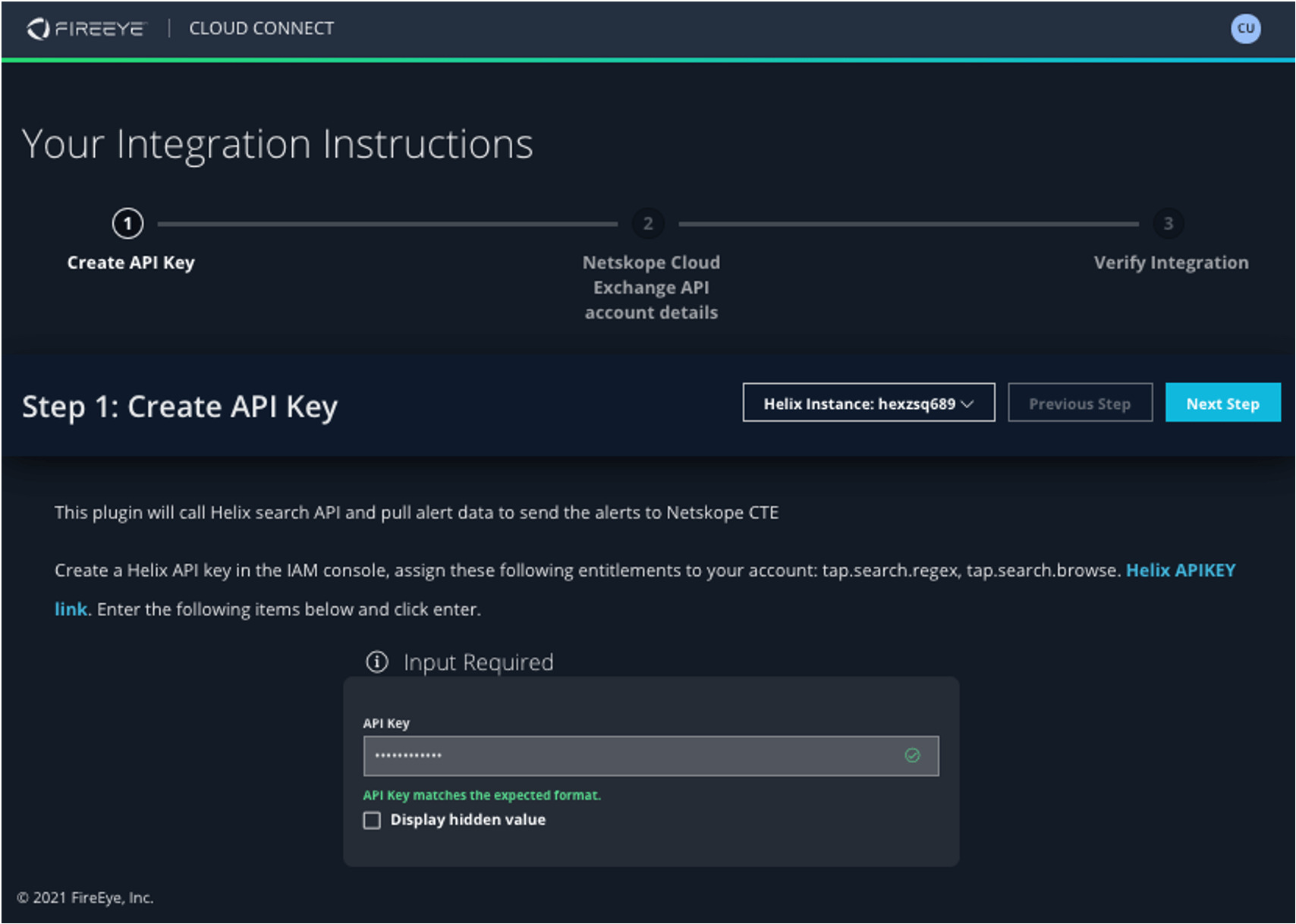
Sharing is Caring: FireEye Helix Connects to Netskope to Block Threats

Feed management API, Chronicle

Frank Cardinale – Personal website of Frank Cardinale
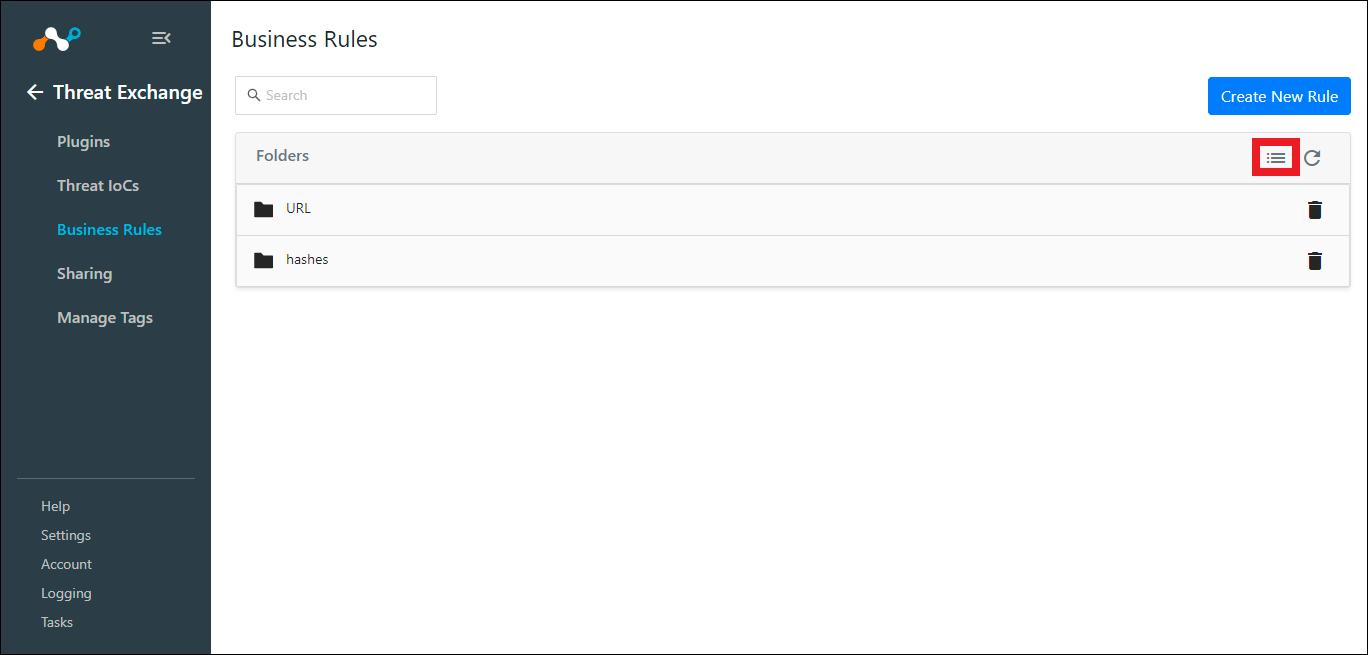
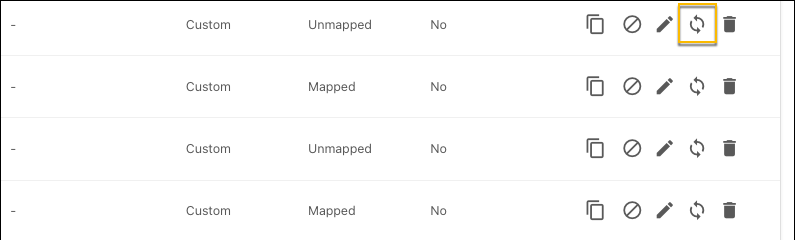
View Threat Exchange Business Rules - Netskope Knowledge Portal
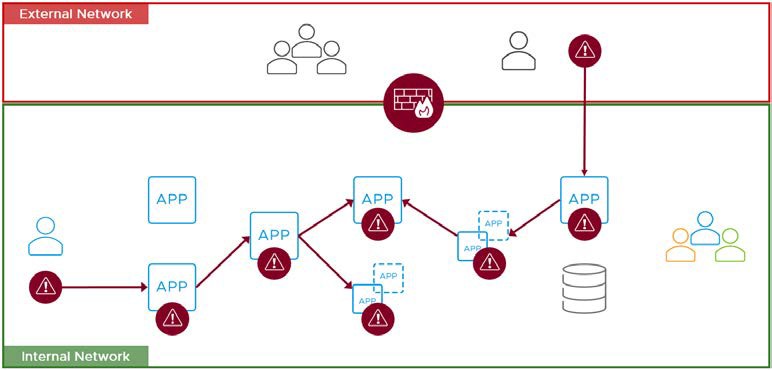
Zero Trust Secure Access to Traditional Applications with VMware

Palo Alto Networks PAN-OS

Shadow cloud apps pose unseen risks

FedRAMP Marketplace
Recomendado para você
-
 SCP-7140 - SCP Foundation15 maio 2024
SCP-7140 - SCP Foundation15 maio 2024 -
 7141-11 Quake Wireless Charging Pad Leed's Promotional Products15 maio 2024
7141-11 Quake Wireless Charging Pad Leed's Promotional Products15 maio 2024 -
ADDENDUM 12] Target has been successfully contained in site-44, Testi15 maio 2024
-
Brandon Jackson on LinkedIn: #amgen #hiringourheroes #biotech15 maio 2024
-
 The Little Mermaid Press Conference Highlights Part 215 maio 2024
The Little Mermaid Press Conference Highlights Part 215 maio 2024 -
 SCP-58725 Existence Eater, Wiki15 maio 2024
SCP-58725 Existence Eater, Wiki15 maio 2024 -
 Mutos in Love Sticker for Sale by jamaziing15 maio 2024
Mutos in Love Sticker for Sale by jamaziing15 maio 2024 -
 Omilik AC Adapter compatible with Condor Model: HK-H5-A05 P/N: SA-054A0IV 745-7141 I.T.E Power Cord15 maio 2024
Omilik AC Adapter compatible with Condor Model: HK-H5-A05 P/N: SA-054A0IV 745-7141 I.T.E Power Cord15 maio 2024 -
 SCP-4264-J, Wiki15 maio 2024
SCP-4264-J, Wiki15 maio 2024 -
 A Unique Role of the Human Cytomegalovirus Small Capsid Protein in Capsid Assembly15 maio 2024
A Unique Role of the Human Cytomegalovirus Small Capsid Protein in Capsid Assembly15 maio 2024
você pode gostar
-
Ludopedia - 🤷♂️ #boardgames #ludopedia #bgbr #jogosdetabuleiro #rpgdemesa #ludomemes15 maio 2024
-
 big sussy fortnite balls (@supersussybaka1) / X15 maio 2024
big sussy fortnite balls (@supersussybaka1) / X15 maio 2024 -
 TV Animation Summer Time Rendering Original Soundtrack15 maio 2024
TV Animation Summer Time Rendering Original Soundtrack15 maio 2024 -
 Free Sonic Coloring Games, Download Free Sonic Coloring Games png15 maio 2024
Free Sonic Coloring Games, Download Free Sonic Coloring Games png15 maio 2024 -
 Scary Teacher 3D APK Download 100% Working - Panda Helper15 maio 2024
Scary Teacher 3D APK Download 100% Working - Panda Helper15 maio 2024 -
 Product Family Catalani La Wally Renata Tebaldi15 maio 2024
Product Family Catalani La Wally Renata Tebaldi15 maio 2024 -
 Jogo Banco Imobiliário Júnior Estrela15 maio 2024
Jogo Banco Imobiliário Júnior Estrela15 maio 2024 -
 Play snake io game online with friends15 maio 2024
Play snake io game online with friends15 maio 2024 -
 Cadeira de Barbeiro Reclinável Pelegrin Couro PU Preto PEL-S040 - CHINA LINK - Compre Direto do Importador15 maio 2024
Cadeira de Barbeiro Reclinável Pelegrin Couro PU Preto PEL-S040 - CHINA LINK - Compre Direto do Importador15 maio 2024 -
 Coloração Igora Royal 7.77 Tinta Ruivo Cobre Schwarzkopf15 maio 2024
Coloração Igora Royal 7.77 Tinta Ruivo Cobre Schwarzkopf15 maio 2024
![ADDENDUM 12] Target has been successfully contained in site-44, Testi](https://www.tiktok.com/api/img/?itemId=7237942448075394330&location=0&aid=1988)

