Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 12 junho 2024

Describing activities of a crime group attacking Ukraine.

US20080120240A1 - Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management - Google Patents

Targeted Cyberattacks: A Superset of Advanced Persistent Threats

Initial access brokers: How are IABs related to the rise in ransomware attacks?
Full article: From cold to cyber warriors: the origins and expansion of NSA's Tailored Access Operations (TAO) to Shadow Brokers

⚖️ LWIL #25: Copyright Claims Board, Algorithm Lawsuits, Location Data Rules and More
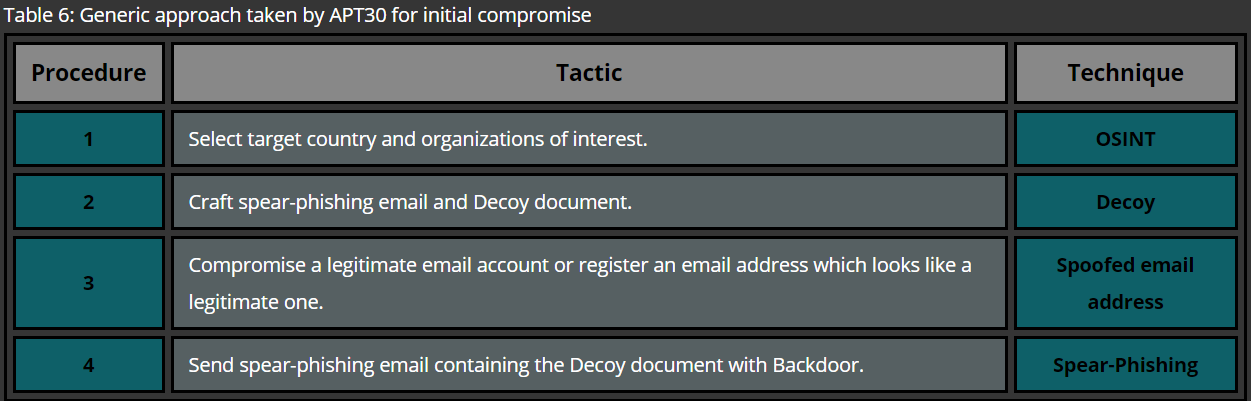
Initial Compromise

Toward a New Momentum: Trend Micro Security Predictions for 2022 - Security Predictions

ISACA Now Blog Global Perspectives & Real-Time Insights

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat
Recomendado para você
-
 Economic Consulting & Strategy - Analysis Group12 junho 2024
Economic Consulting & Strategy - Analysis Group12 junho 2024 -
 Q&A: For Bates interns, there's 'no better outlet' for economics12 junho 2024
Q&A: For Bates interns, there's 'no better outlet' for economics12 junho 2024 -
 Working at Analysis Group12 junho 2024
Working at Analysis Group12 junho 2024 -
Derek Vicino - Vice President of Finance - Analysis Group12 junho 2024
-
 HRDAG – Human Rights Data Analysis Group12 junho 2024
HRDAG – Human Rights Data Analysis Group12 junho 2024 -
 Annual Meeting of the Lunar Exploration Analysis Group12 junho 2024
Annual Meeting of the Lunar Exploration Analysis Group12 junho 2024 -
 Administrative Staff - Analysis Group12 junho 2024
Administrative Staff - Analysis Group12 junho 2024 -
 IAG is Leading AI powered Drug Development and Precision Medicine12 junho 2024
IAG is Leading AI powered Drug Development and Precision Medicine12 junho 2024 -
Target Analysis Group12 junho 2024
-
 Analysis Team – Analysis, Reporting & Planning Solutions12 junho 2024
Analysis Team – Analysis, Reporting & Planning Solutions12 junho 2024
você pode gostar
-
 How to get Shiny Galarian Articuno, Zapdos and Moltres in Pokemon Sword & Shield - Dexerto12 junho 2024
How to get Shiny Galarian Articuno, Zapdos and Moltres in Pokemon Sword & Shield - Dexerto12 junho 2024 -
 Desenho Animado de Séries e Filmes Clássicos! Anos 80 e 9012 junho 2024
Desenho Animado de Séries e Filmes Clássicos! Anos 80 e 9012 junho 2024 -
 🔥 Adachi offers to play fortnite with you, what you do12 junho 2024
🔥 Adachi offers to play fortnite with you, what you do12 junho 2024 -
 EA Sports FC 24 Web App & Companion App: info and release dates12 junho 2024
EA Sports FC 24 Web App & Companion App: info and release dates12 junho 2024 -
 Suki na Ko ga Megane wo Wasureta12 junho 2024
Suki na Ko ga Megane wo Wasureta12 junho 2024 -
 14pcs Alphabet Lore Plush Toy Anime Letters Stuffed Toys12 junho 2024
14pcs Alphabet Lore Plush Toy Anime Letters Stuffed Toys12 junho 2024 -
Dungeon ni Deai wo Motomeru no wa Machigatteiru Darou ka? Season 5 Officially Confirmed with Trailer and Key Visual12 junho 2024
-
 Championship predictor: What will final 2018-19 table look like12 junho 2024
Championship predictor: What will final 2018-19 table look like12 junho 2024 -
 NEW* ALL WORKING UPDATE CODES FOR ANIME ADVENTURES! ROBLOX ANIME ADVENTURES CODES12 junho 2024
NEW* ALL WORKING UPDATE CODES FOR ANIME ADVENTURES! ROBLOX ANIME ADVENTURES CODES12 junho 2024 -
 A Message from our CEO and Co-Founder Vlad Tenev - Robinhood Newsroom12 junho 2024
A Message from our CEO and Co-Founder Vlad Tenev - Robinhood Newsroom12 junho 2024


