Malware analysis
Por um escritor misterioso
Last updated 12 maio 2024

Detecting Out-of-Band Malware with NVIDIA BlueField DPU

TryHackMe Malware Analysis

Malware Analysis: SharkBot

iLabAfrica – Malware Analysis for Incident Handlers

What is Malware Analysis and How It Unveils the Anatomy of Malicious Software - Article by CyberNX
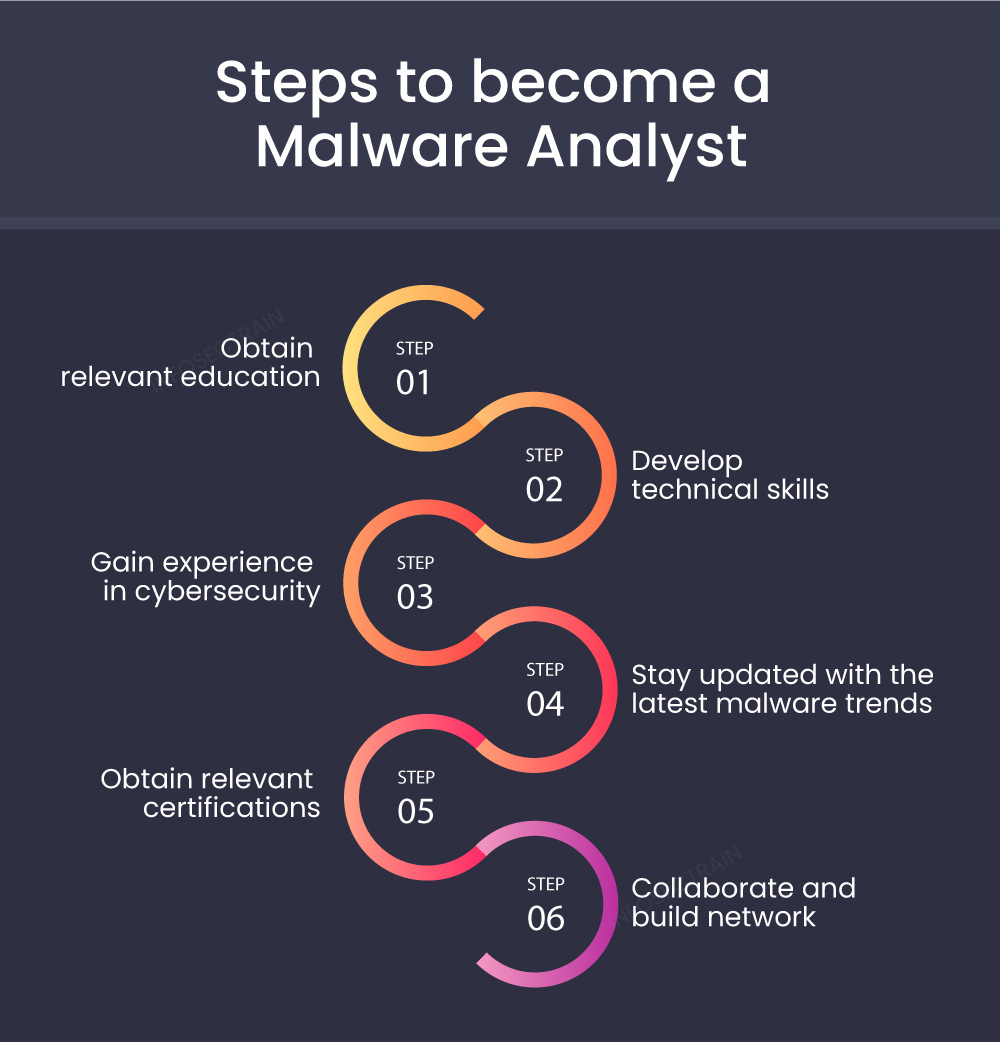
How to become a Malware Analyst? - InfosecTrain

How Malware Analysis Works - NetWitness Community - 669511

Malware Analyst – Job Description and How to Become - Security Boulevard
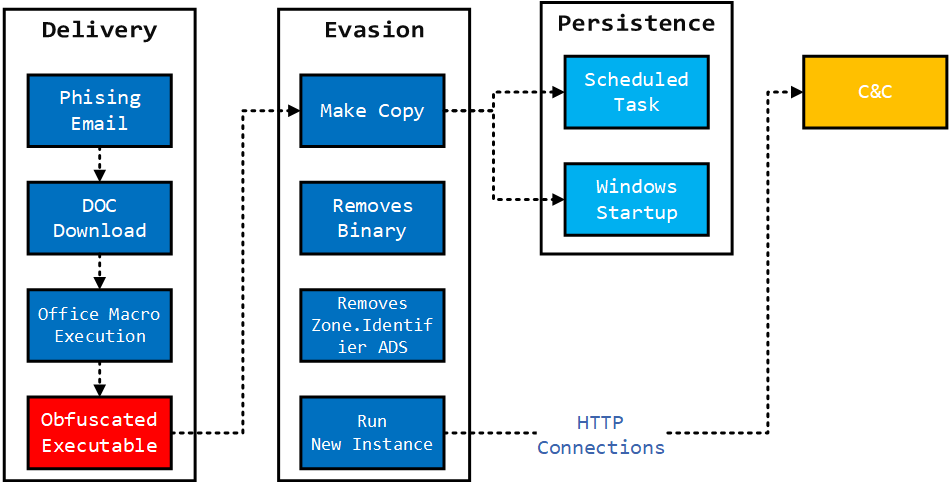
Advanced Windows Malware Analysis - Acquiring Memory Artifacts

A basic malware analysis method - ScienceDirect

Malware Analysis: Steps & Examples - CrowdStrike
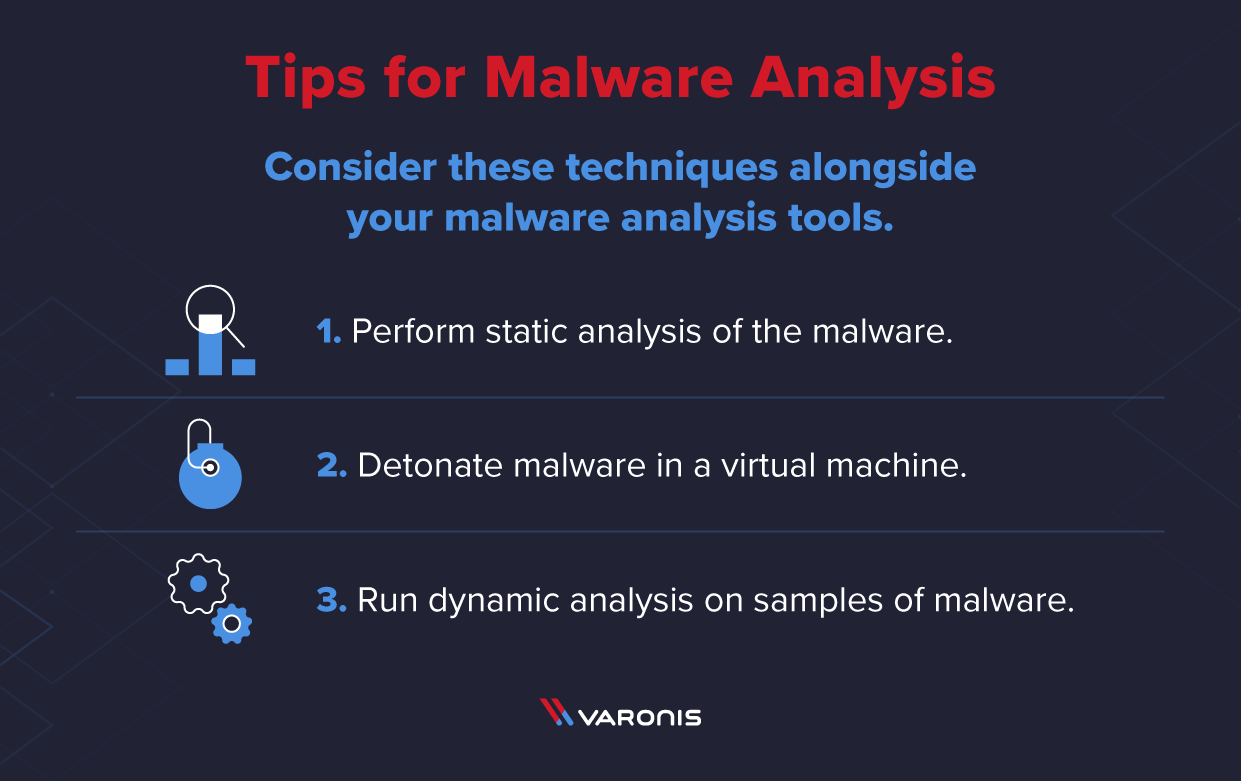
11 Best Malware Analysis Tools and Their Features
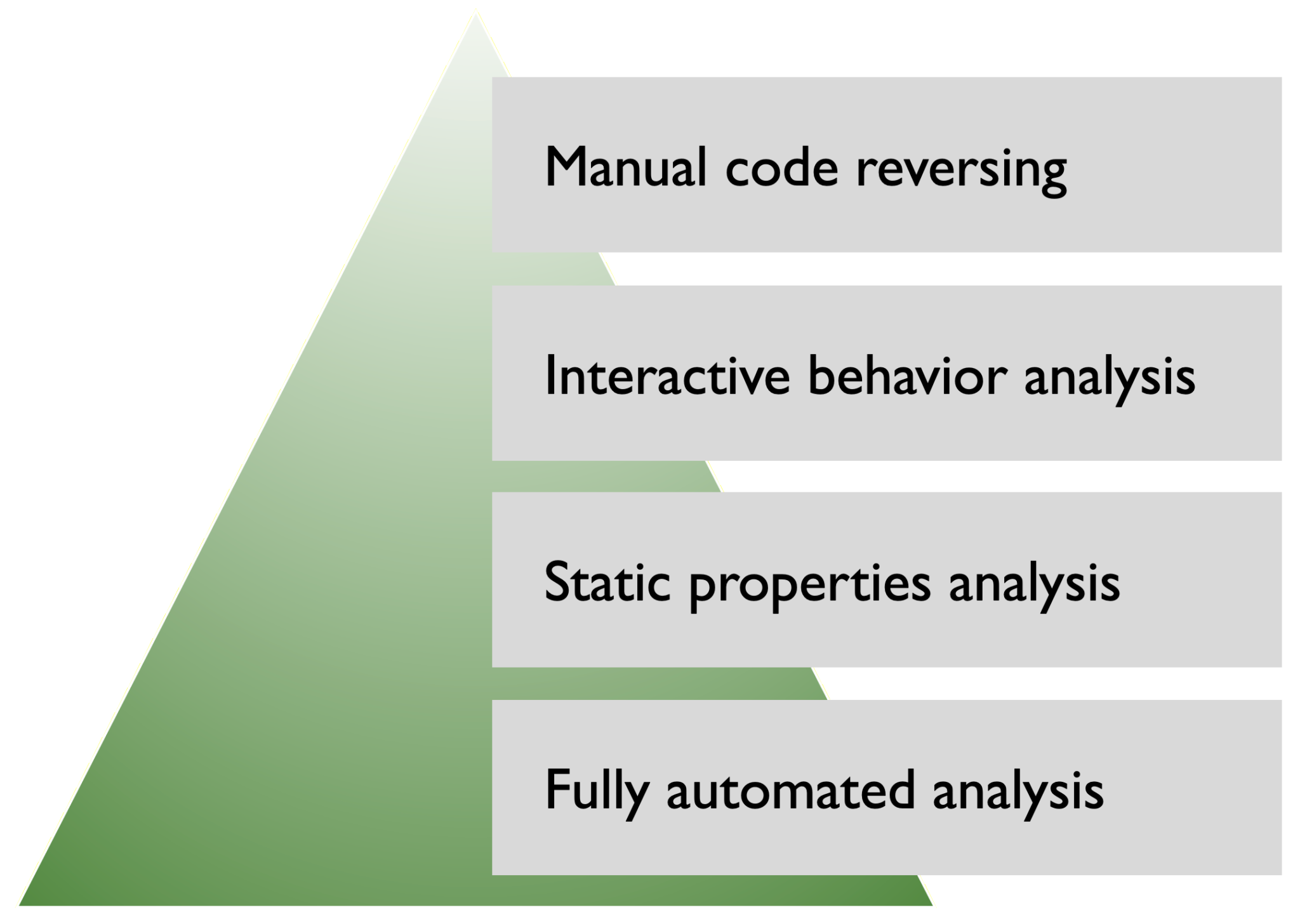
How You Can Start Learning Malware Analysis
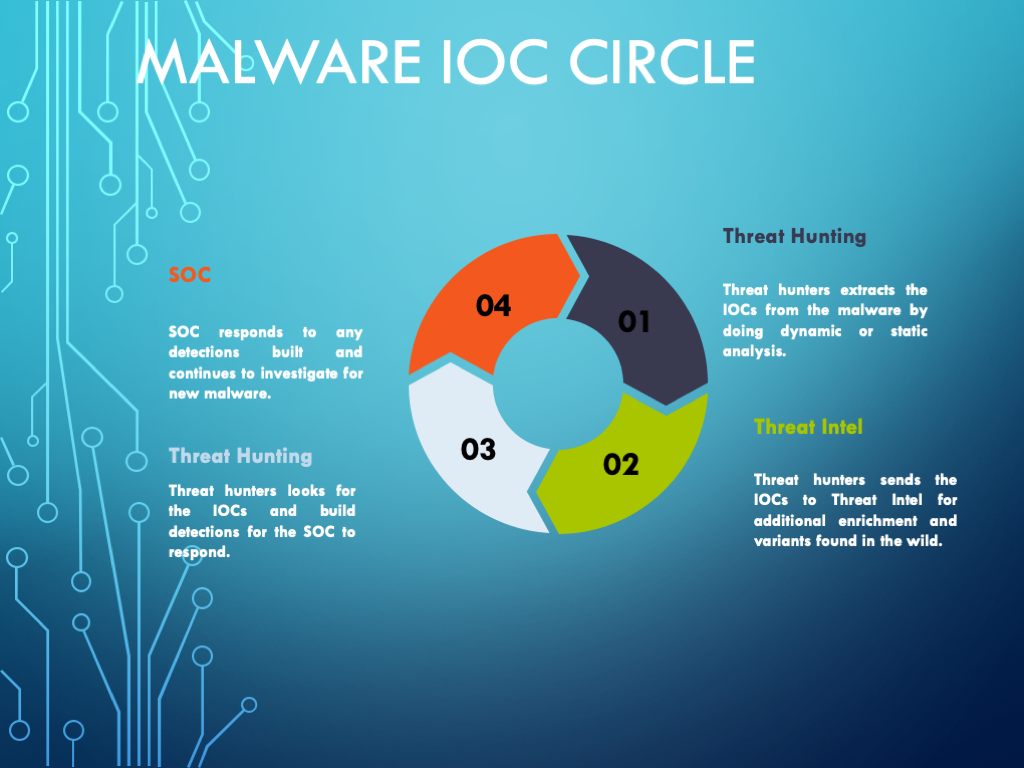
Malware Analysis Framework v1.0
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+
Recomendado para você
-
 Angry And Happy on X: @Roblox Plz banned this game @Roblox if you12 maio 2024
Angry And Happy on X: @Roblox Plz banned this game @Roblox if you12 maio 2024 -
 Roblox: The children's game with a sex problem - BBC News12 maio 2024
Roblox: The children's game with a sex problem - BBC News12 maio 2024 -
 How to find condo game links in Roblox in May/June 2022 - Quora12 maio 2024
How to find condo game links in Roblox in May/June 2022 - Quora12 maio 2024 -
 🔥HOW TO FIND Roblox Scented Con Games🔥ODER GAME 🔥Roblox Condo12 maio 2024
🔥HOW TO FIND Roblox Scented Con Games🔥ODER GAME 🔥Roblox Condo12 maio 2024 -
2022 roblox condo games|TikTok Search12 maio 2024
-
free roblox #condogameroblox, condogameroblox12 maio 2024
-
condo game links|TikTok Search12 maio 2024
-
So I saw my friend playing a game that had a weird title. My curious mind wanted to see what game it is so I joined him. As soon as I joined12 maio 2024
-
 How to find condo game links in Roblox in January 2022 - Quora12 maio 2024
How to find condo game links in Roblox in January 2022 - Quora12 maio 2024 -
 ROBLOX CONDO LINK (SCENTED CONS)12 maio 2024
ROBLOX CONDO LINK (SCENTED CONS)12 maio 2024
você pode gostar
-
 LEGO MOC PIGGY: The Board Game - House by PatrickStarGames12 maio 2024
LEGO MOC PIGGY: The Board Game - House by PatrickStarGames12 maio 2024 -
Arena Desportiva12 maio 2024
-
 Plataforma (PTA/ PEMT) Tipo Tesoura - Pantográfica - JLG 2030 para Trabalho em Altura até 8 metros - Guindastes Cunzolo - Campinas, São José dos Campos, Sorocaba, Taubaté - SP e Três Lagoas - MS12 maio 2024
Plataforma (PTA/ PEMT) Tipo Tesoura - Pantográfica - JLG 2030 para Trabalho em Altura até 8 metros - Guindastes Cunzolo - Campinas, São José dos Campos, Sorocaba, Taubaté - SP e Três Lagoas - MS12 maio 2024 -
 black hair blue eyes long hair necklace pokemon reshiram starshadowmagician sunglasses white hair yellow eyes zekrom12 maio 2024
black hair blue eyes long hair necklace pokemon reshiram starshadowmagician sunglasses white hair yellow eyes zekrom12 maio 2024 -
Xadrez da Didáxis de S. Cosme nos oitavos de final da Taça de12 maio 2024
-
 Izumi Nase (Kyoukai no Kanata) - v1.012 maio 2024
Izumi Nase (Kyoukai no Kanata) - v1.012 maio 2024 -
Fide Chess Rating Calculator – Apps on Google Play12 maio 2024
-
 Domestic Girlfriend, Volume 212 maio 2024
Domestic Girlfriend, Volume 212 maio 2024 -
 Scary Face / Horror / Digital Painting / Digital Art / - Denmark12 maio 2024
Scary Face / Horror / Digital Painting / Digital Art / - Denmark12 maio 2024 -
 A Dama e o Vagabundo – Wikipédia, a enciclopédia livre12 maio 2024
A Dama e o Vagabundo – Wikipédia, a enciclopédia livre12 maio 2024




