Malware analysis Malicious activity
Por um escritor misterioso
Last updated 16 junho 2024
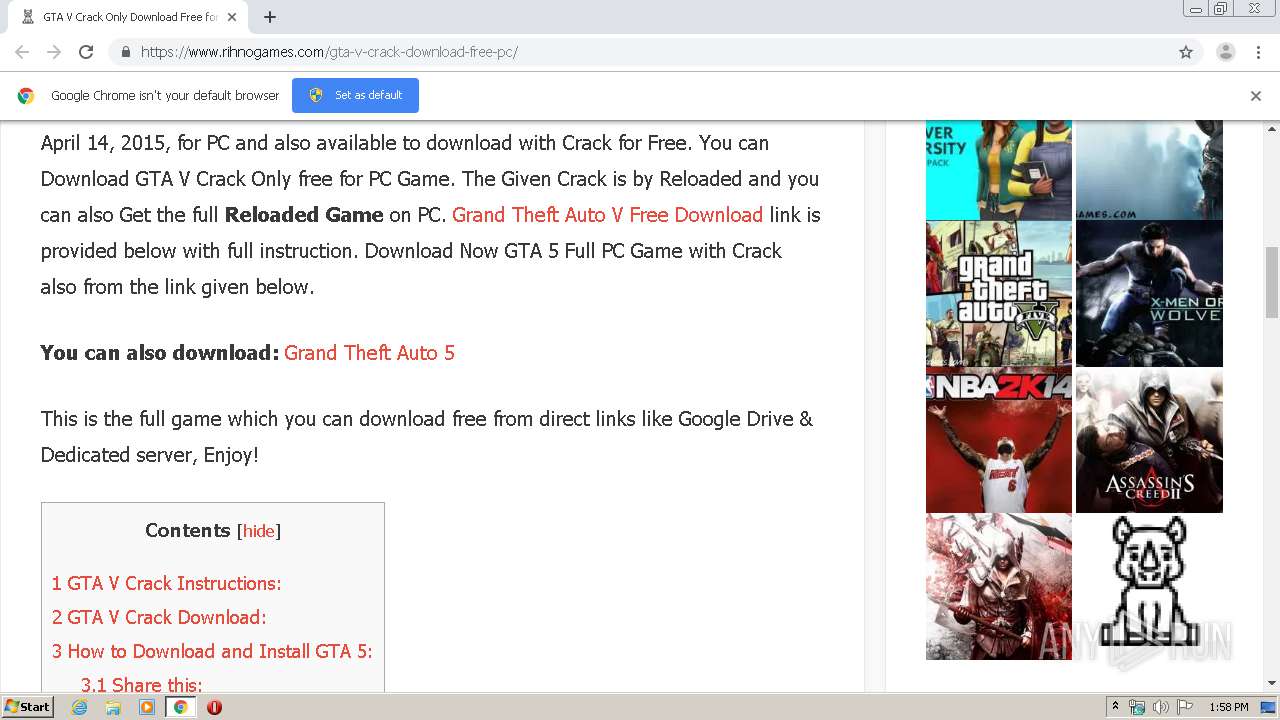

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

How to build a malware analysis sandbox with Elastic Security
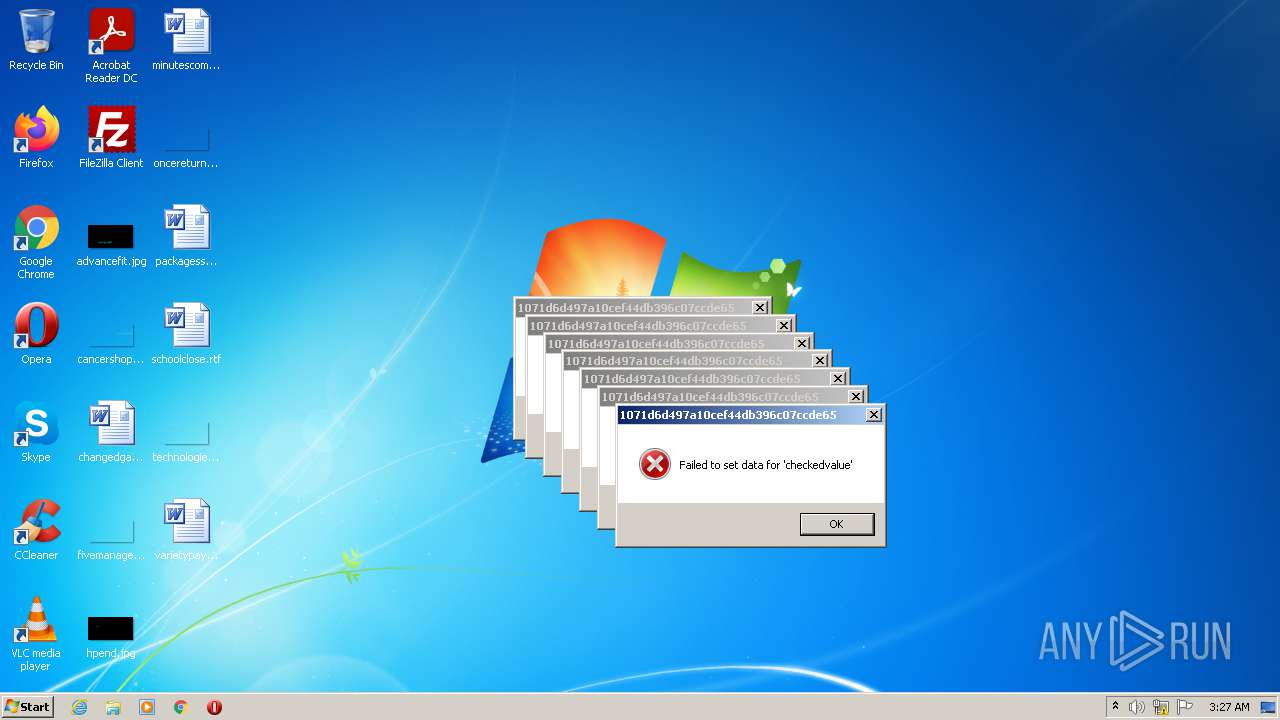
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity
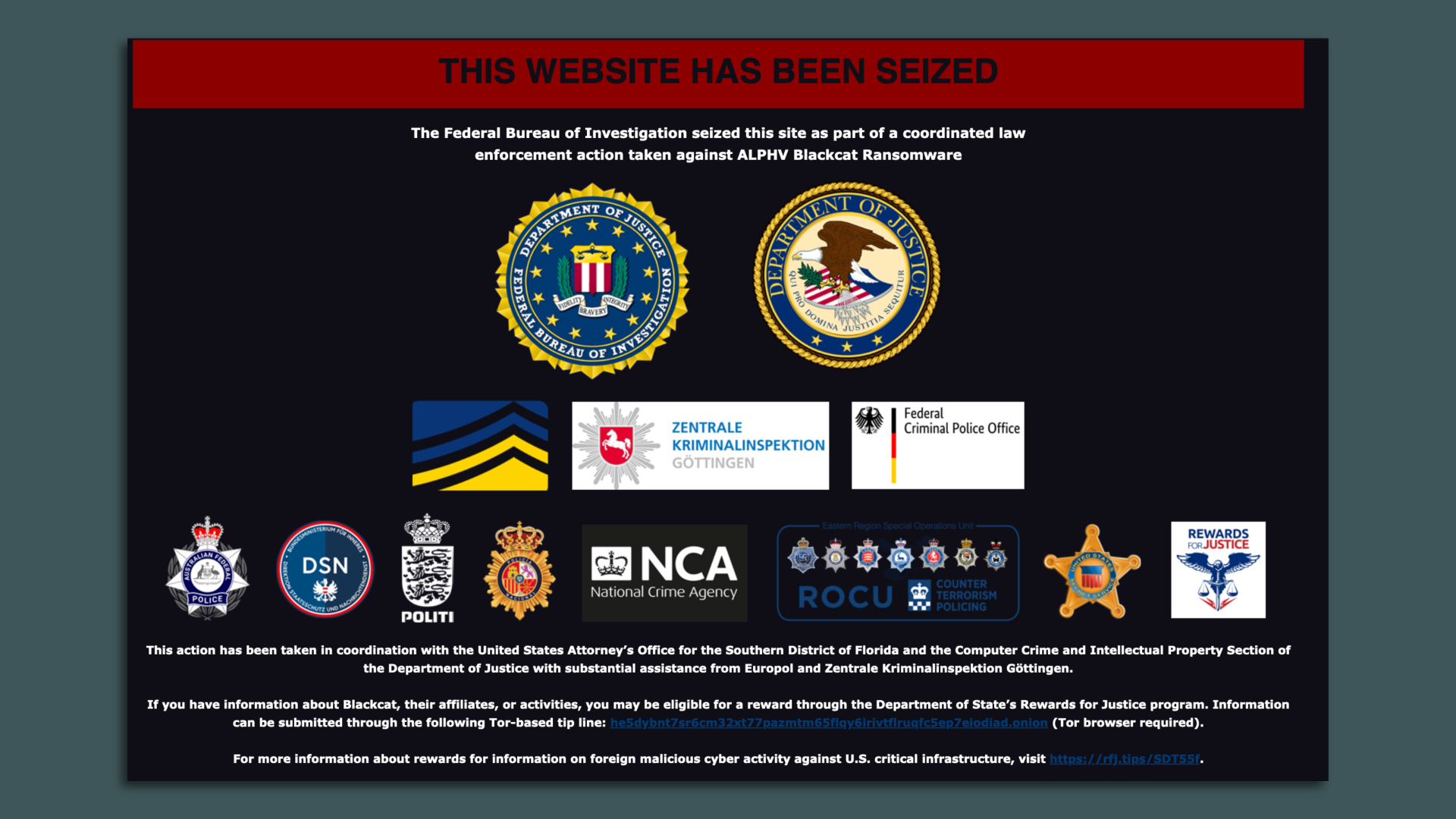
U.S. law enforcement seizes BlackCat ransomware site, distributes decryption key
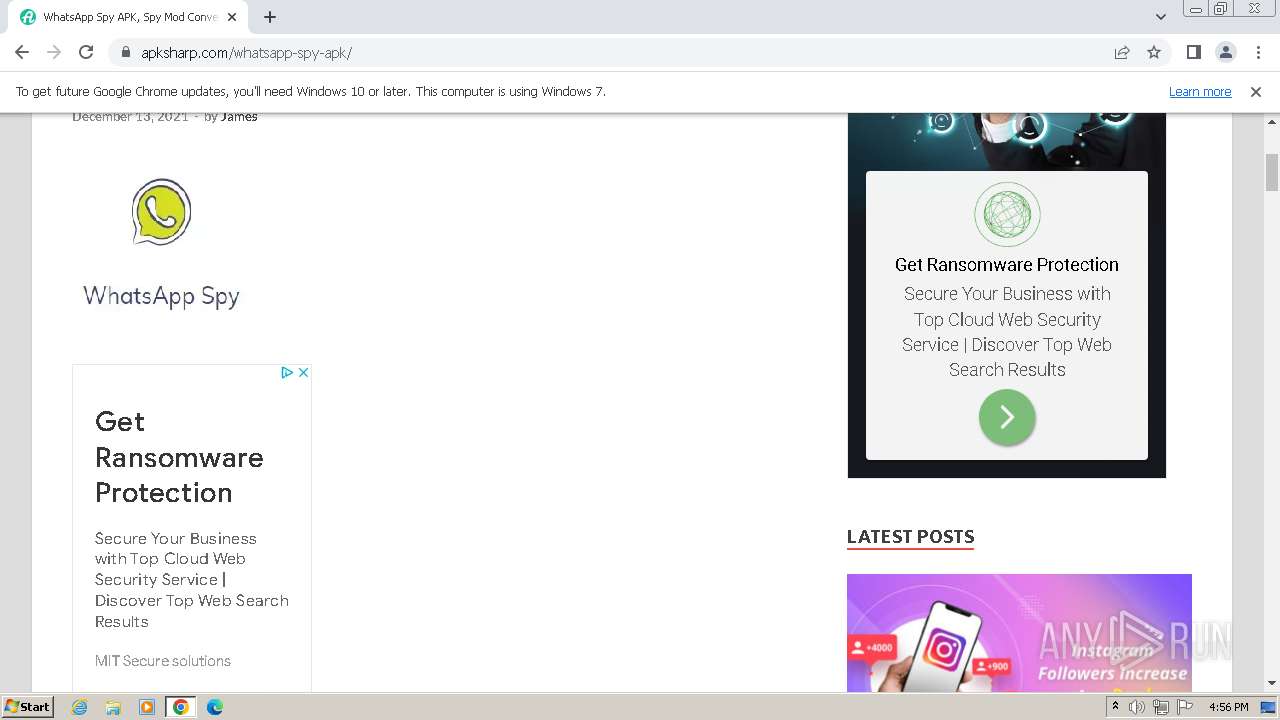
Malware analysis apksharp.com Malicious activity

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Antivirus software - Wikipedia

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Malware analysis mykey_.rar Malicious activity
Recomendado para você
-
 Grand Theft Auto V - Wikipedia16 junho 2024
Grand Theft Auto V - Wikipedia16 junho 2024 -
 GTA V for PC May Be Cancelled - Software Informer16 junho 2024
GTA V for PC May Be Cancelled - Software Informer16 junho 2024 -
 Download HD fonts for 1C crack (v. 1.01) for GTA San Andreas16 junho 2024
Download HD fonts for 1C crack (v. 1.01) for GTA San Andreas16 junho 2024 -
 chirag on X: Download and play Grand theft auto V (GTA V) for16 junho 2024
chirag on X: Download and play Grand theft auto V (GTA V) for16 junho 2024 -
 Fix : Steam failed to intialize 100% working in easiest method16 junho 2024
Fix : Steam failed to intialize 100% working in easiest method16 junho 2024 -
 How to install Gta V, Crack File16 junho 2024
How to install Gta V, Crack File16 junho 2024 -
 Download GTA V v1.0.2628-GOLDBERG16 junho 2024
Download GTA V v1.0.2628-GOLDBERG16 junho 2024 -
How to download gta v on cd keys|TikTok Search16 junho 2024
-
 Download Crack by Razor1911 (For Episodes) for GTA 416 junho 2024
Download Crack by Razor1911 (For Episodes) for GTA 416 junho 2024 -
 Grand Theft Auto V: Premium Edition Download GTA V for PC Today - Epic Games Store16 junho 2024
Grand Theft Auto V: Premium Edition Download GTA V for PC Today - Epic Games Store16 junho 2024
você pode gostar
-
Pokémon - watch tv show streaming online16 junho 2024
-
 December 5 (9am - 12pm CST) IN PERSON TICKET - Hotheads Custom Coloring Extensions Demo - 23/12/05IIA16 junho 2024
December 5 (9am - 12pm CST) IN PERSON TICKET - Hotheads Custom Coloring Extensions Demo - 23/12/05IIA16 junho 2024 -
 Petition · SAY NO TO THE ROBLOX TRADE COOLDOWN! ·16 junho 2024
Petition · SAY NO TO THE ROBLOX TRADE COOLDOWN! ·16 junho 2024 -
 Call of Duty - Modern Warfare 2 Spec Ops (2009) MP3 - Download Call of Duty - Modern Warfare 2 Spec Ops (2009) Soundtracks for FREE!16 junho 2024
Call of Duty - Modern Warfare 2 Spec Ops (2009) MP3 - Download Call of Duty - Modern Warfare 2 Spec Ops (2009) Soundtracks for FREE!16 junho 2024 -
 MelonDS 0.9.3, Death Note Kira Game (English Patched)16 junho 2024
MelonDS 0.9.3, Death Note Kira Game (English Patched)16 junho 2024 -
Buy Call of Duty®: Advanced Warfare Gold Edition16 junho 2024
-
 ATUVOS Luggage Tracker, Key Finder, Smart Bluetooth Tracker Pairs with Apple Find My (iOS Only), Item Locator for Bags, Wallets, Keys, Waterproof IP67, Anti-Los… in 202316 junho 2024
ATUVOS Luggage Tracker, Key Finder, Smart Bluetooth Tracker Pairs with Apple Find My (iOS Only), Item Locator for Bags, Wallets, Keys, Waterproof IP67, Anti-Los… in 202316 junho 2024 -
 I enjoy collecting bad Xbox 360 games, I consider these to be the best of the worst of my collection. : r/xbox36016 junho 2024
I enjoy collecting bad Xbox 360 games, I consider these to be the best of the worst of my collection. : r/xbox36016 junho 2024 -
sonic 4 o filme|Pesquisa do TikTok16 junho 2024
-
 Dave Thomas on X: @marathontalk have either of you done the Midnight Sun Marathon in Tromso in the Artic Circle / top of Norway - I did it on Sat night16 junho 2024
Dave Thomas on X: @marathontalk have either of you done the Midnight Sun Marathon in Tromso in the Artic Circle / top of Norway - I did it on Sat night16 junho 2024



