Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 01 junho 2024

7 Benefits Of Dynamic Malware Analysis

Malware Analysis 101 - Basic Static Analysis
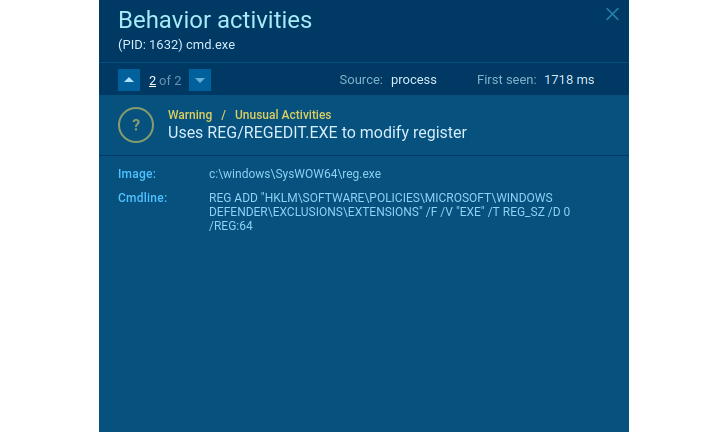
How to Detect New Threats via Suspicious Activities
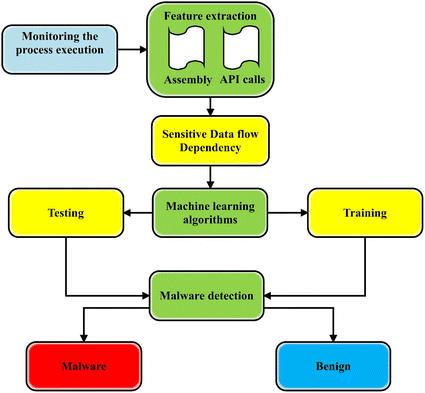
A state-of-the-art survey of malware detection approaches using

Malware Detection: 7 Methods and Security Solutions that Use Them
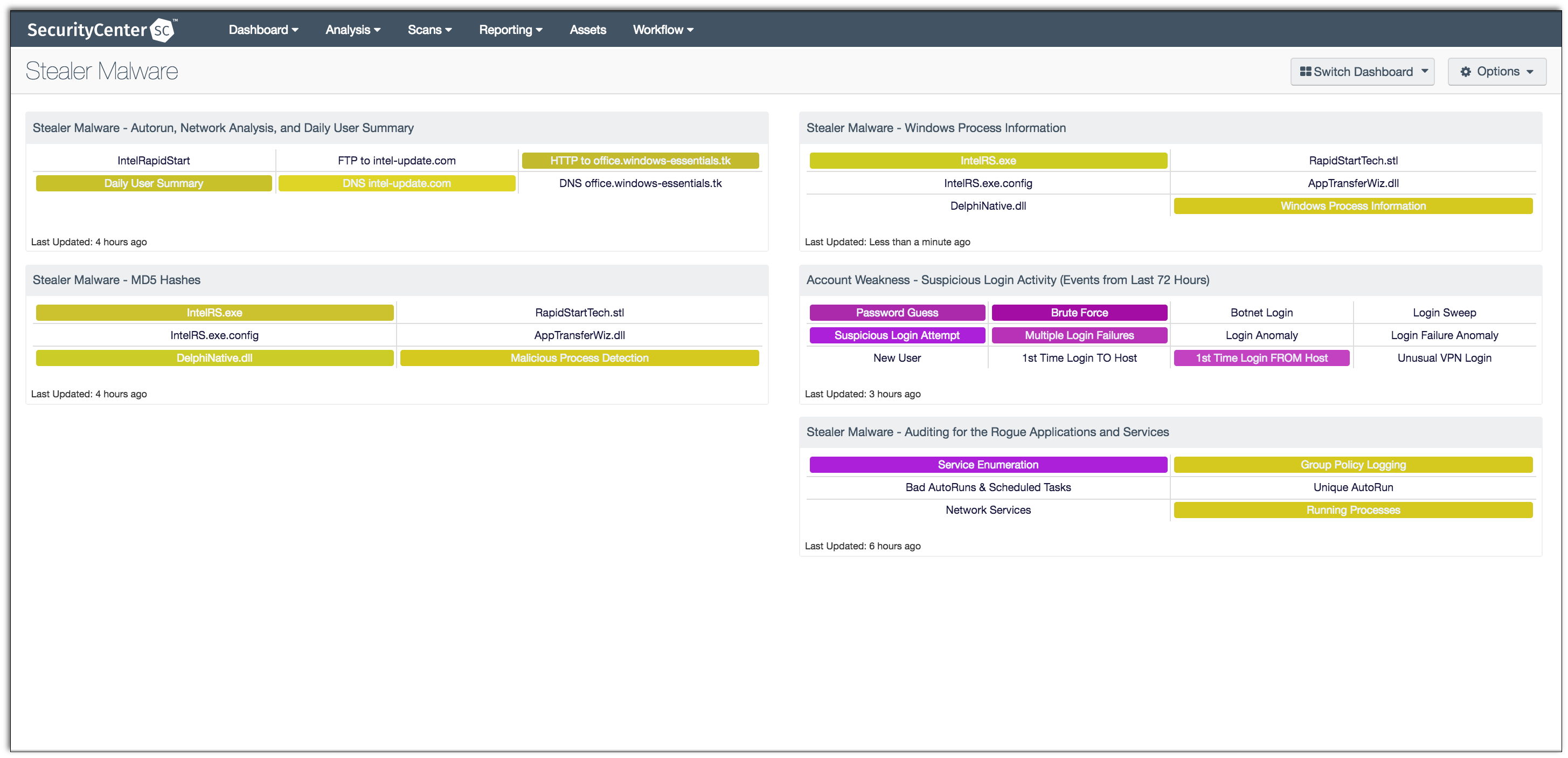
Stealer Malware - SC Dashboard

How AI is shaping malware analysis ~ VirusTotal Blog

How to Detect New Threats via Suspicious Activities
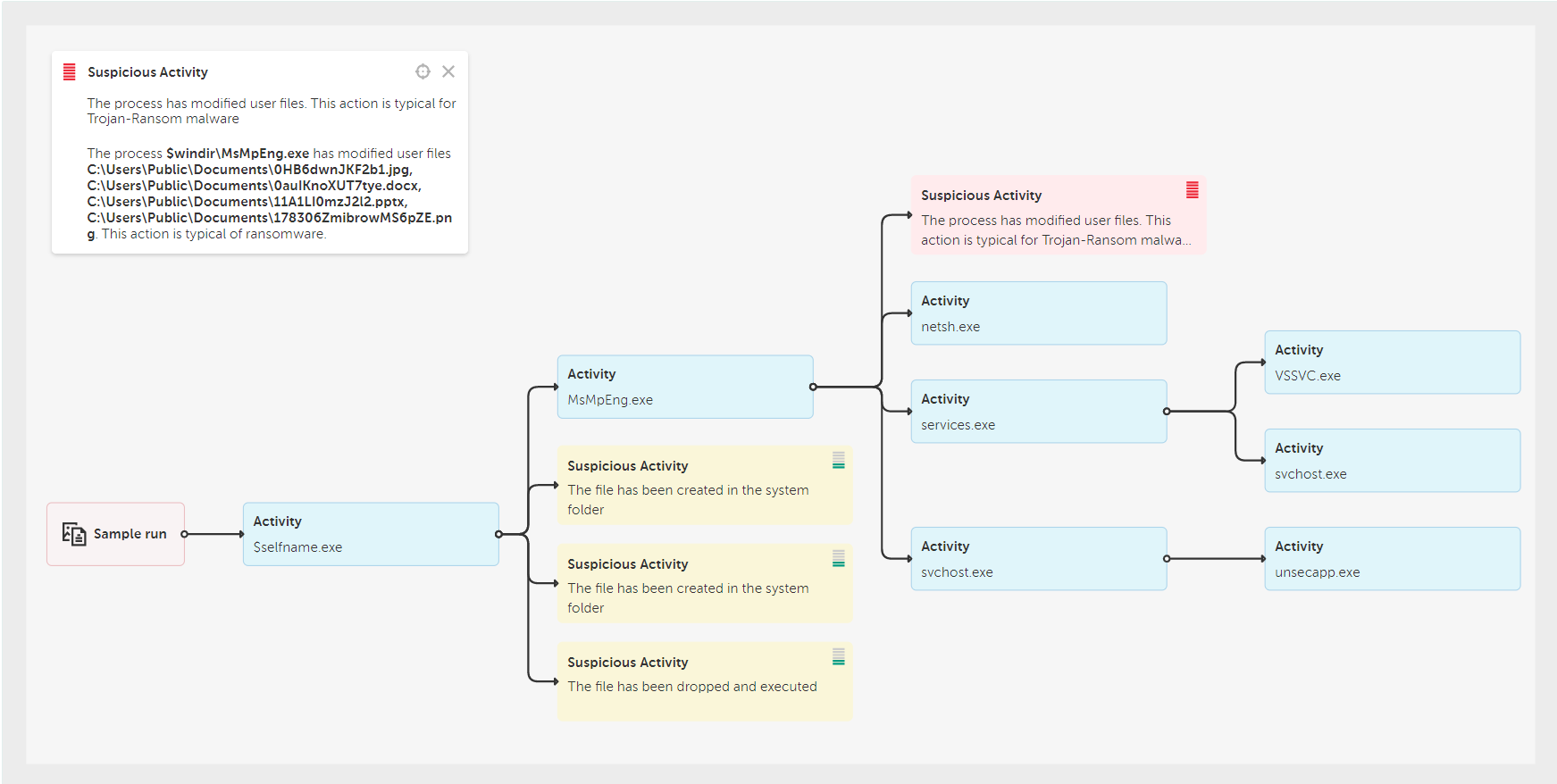
REvil ransomware attack against MSPs and its clients around the
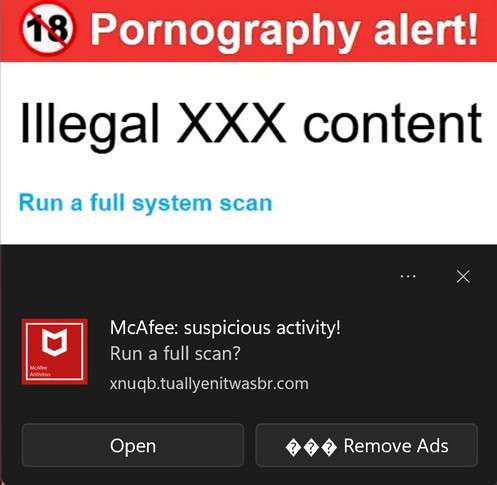
Remove McAfee Suspicious Activity Pop-ups [Virus Removal]

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
WRT - Ever NEED to know your IP ADDRESS? When syncing security cameras & other smart home devices, you sometimes need to re-configure your IP address. Simple go to www.ipchicken.com & it01 junho 2024
-
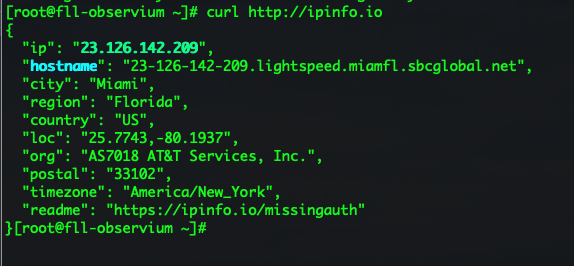 Doing “IP Chicken” from the CLI – InfoSec Monkey01 junho 2024
Doing “IP Chicken” from the CLI – InfoSec Monkey01 junho 2024 -
 Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders01 junho 2024
Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders01 junho 2024 -
 Instant Pot Archives - Kravings Food Adventures01 junho 2024
Instant Pot Archives - Kravings Food Adventures01 junho 2024 -
After exchanging my SWITCH to a ROUTER, I… - Apple Community01 junho 2024
-
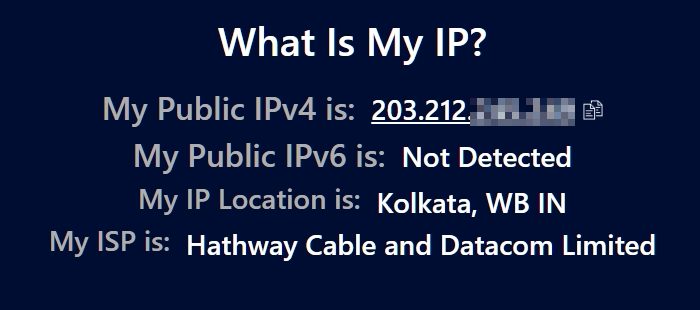 What's My IP Address and How to Find It01 junho 2024
What's My IP Address and How to Find It01 junho 2024 -
 ipchicken Hypixel Forums01 junho 2024
ipchicken Hypixel Forums01 junho 2024 -
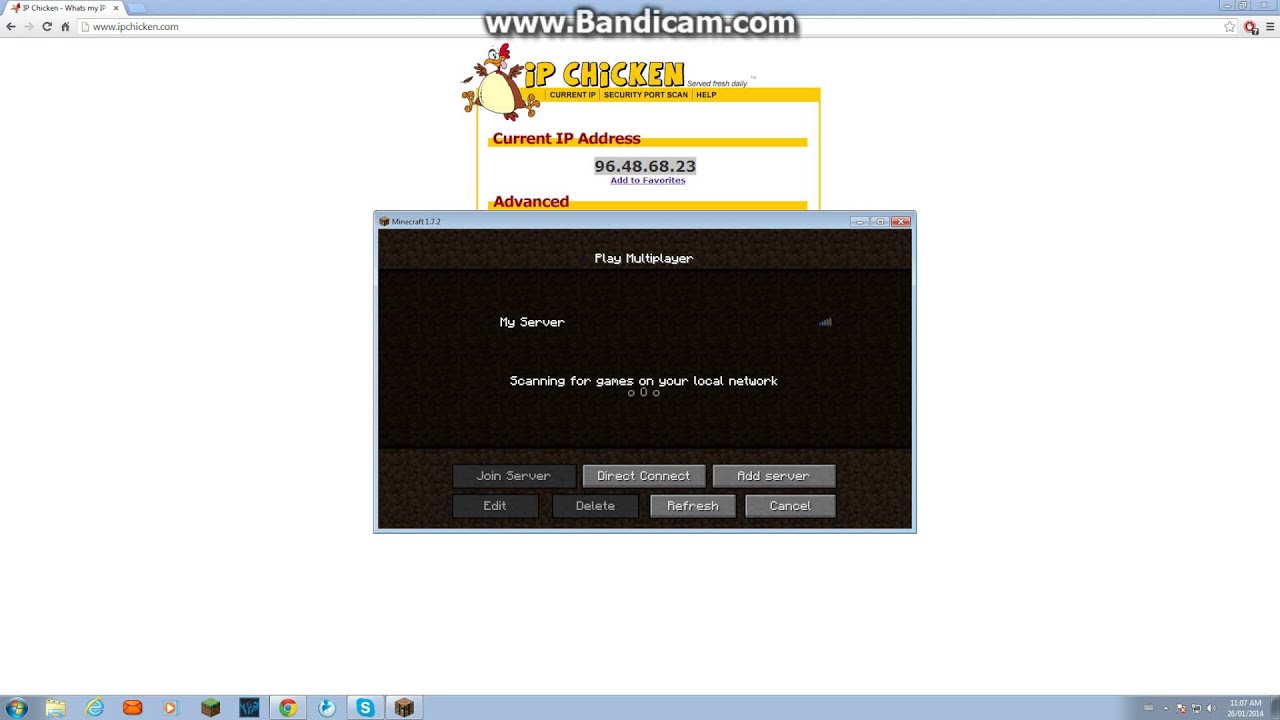 How to use ipchicken to access your minecraft server01 junho 2024
How to use ipchicken to access your minecraft server01 junho 2024 -
 Instant Pot Chicken Salad with Strawberries, Feta, and Pecans - Pesto & Margaritas01 junho 2024
Instant Pot Chicken Salad with Strawberries, Feta, and Pecans - Pesto & Margaritas01 junho 2024 -
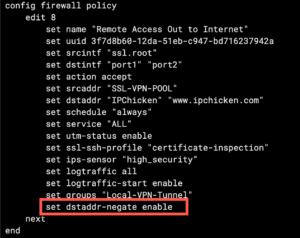 Direct Access through Split Tunnel VPN – InfoSec Monkey01 junho 2024
Direct Access through Split Tunnel VPN – InfoSec Monkey01 junho 2024
você pode gostar
-
 Acalagon the black (LOTR) vs Skyrim Dragons - Battles - Comic Vine01 junho 2024
Acalagon the black (LOTR) vs Skyrim Dragons - Battles - Comic Vine01 junho 2024 -
 KNVB divulga as novas camisas da seleção masculina e feminina01 junho 2024
KNVB divulga as novas camisas da seleção masculina e feminina01 junho 2024 -
/cdn.vox-cdn.com/uploads/chorus_image/image/54462143/The_Last_Guardian__20170212211737.0.jpg) The Last Guardian contains a beautiful lesson about animals' ability to forgive - Polygon01 junho 2024
The Last Guardian contains a beautiful lesson about animals' ability to forgive - Polygon01 junho 2024 -
 Amazing New Ready Player One Posters Take On The Matrix, Back To01 junho 2024
Amazing New Ready Player One Posters Take On The Matrix, Back To01 junho 2024 -
 Create a Anime Adventures (MYTHICS EVO Update 6 with Yuto) Tier01 junho 2024
Create a Anime Adventures (MYTHICS EVO Update 6 with Yuto) Tier01 junho 2024 -
 Desenho de Cara de Raposa para colorir01 junho 2024
Desenho de Cara de Raposa para colorir01 junho 2024 -
 Crunchyroll Hime Fleece Blanket - Entertainment Earth01 junho 2024
Crunchyroll Hime Fleece Blanket - Entertainment Earth01 junho 2024 -
 Jogando Jogos Clássicos Tabuleiro Gamão Isolado Xadrez Damas01 junho 2024
Jogando Jogos Clássicos Tabuleiro Gamão Isolado Xadrez Damas01 junho 2024 -
Vídeos Engraçados01 junho 2024
-
Pet Society was a childhood facebook game of mine, so when I saw Pet P01 junho 2024


