TCP Idle Scan (-sI) Nmap Network Scanning
Por um escritor misterioso
Last updated 13 maio 2024
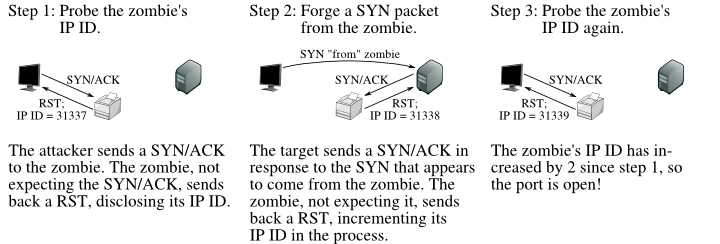

Understanding the NMAP methodology — Part 3, by Jay Vadhaiya
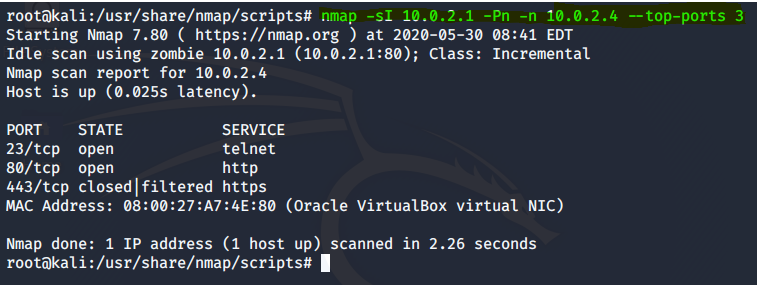
End]Network Vulnerability and Scanning: Other NMAP Scans (NULL,FIN,XMAS,ACK, IDLE), by Koay Yong Cett

NMap > Penetration Testing and Network Defense: Performing Host Reconnaissance

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan

How hackers use idle scans in port scan attacks
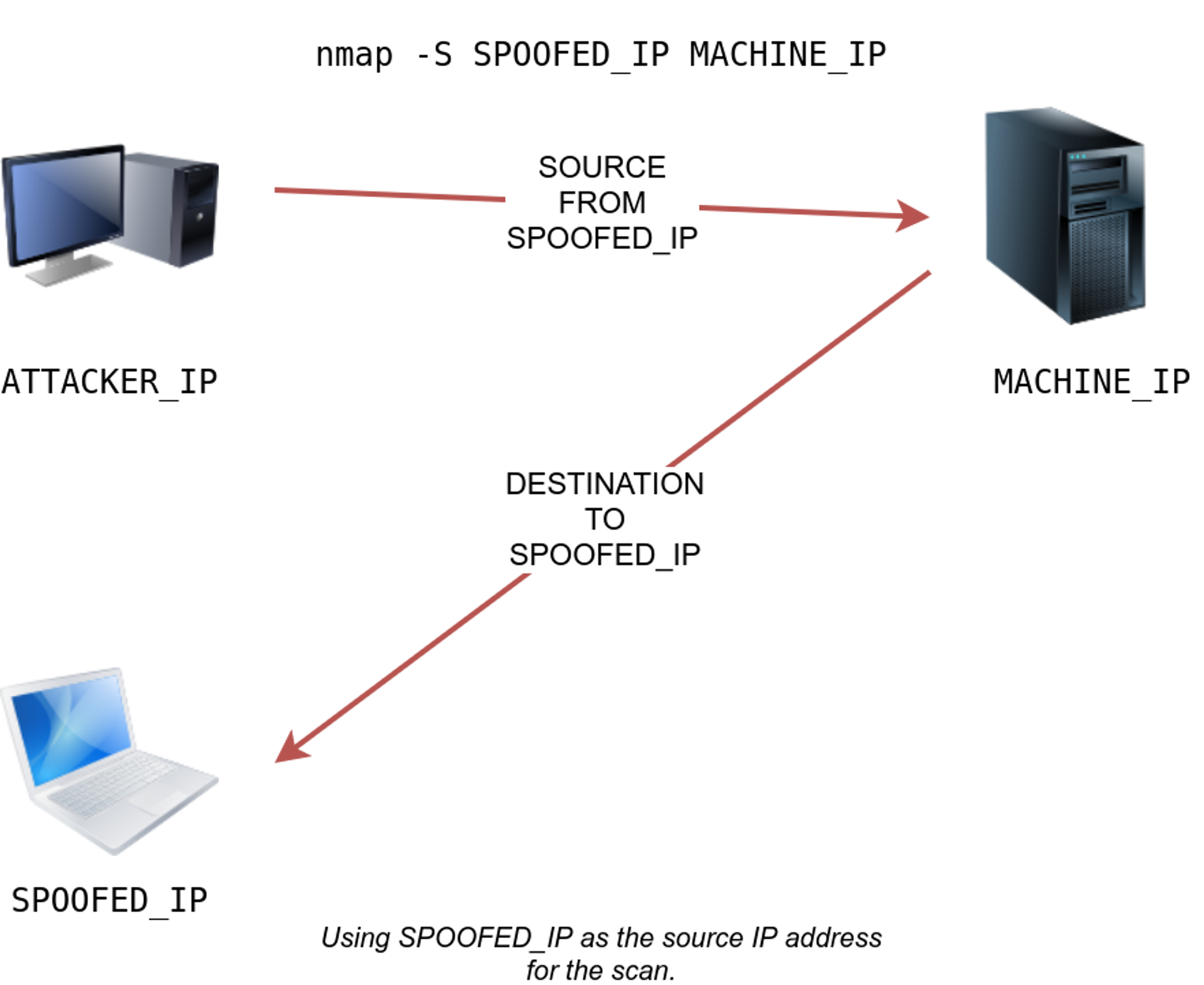
The Ultimate Guide to Port Scanning using Nmap
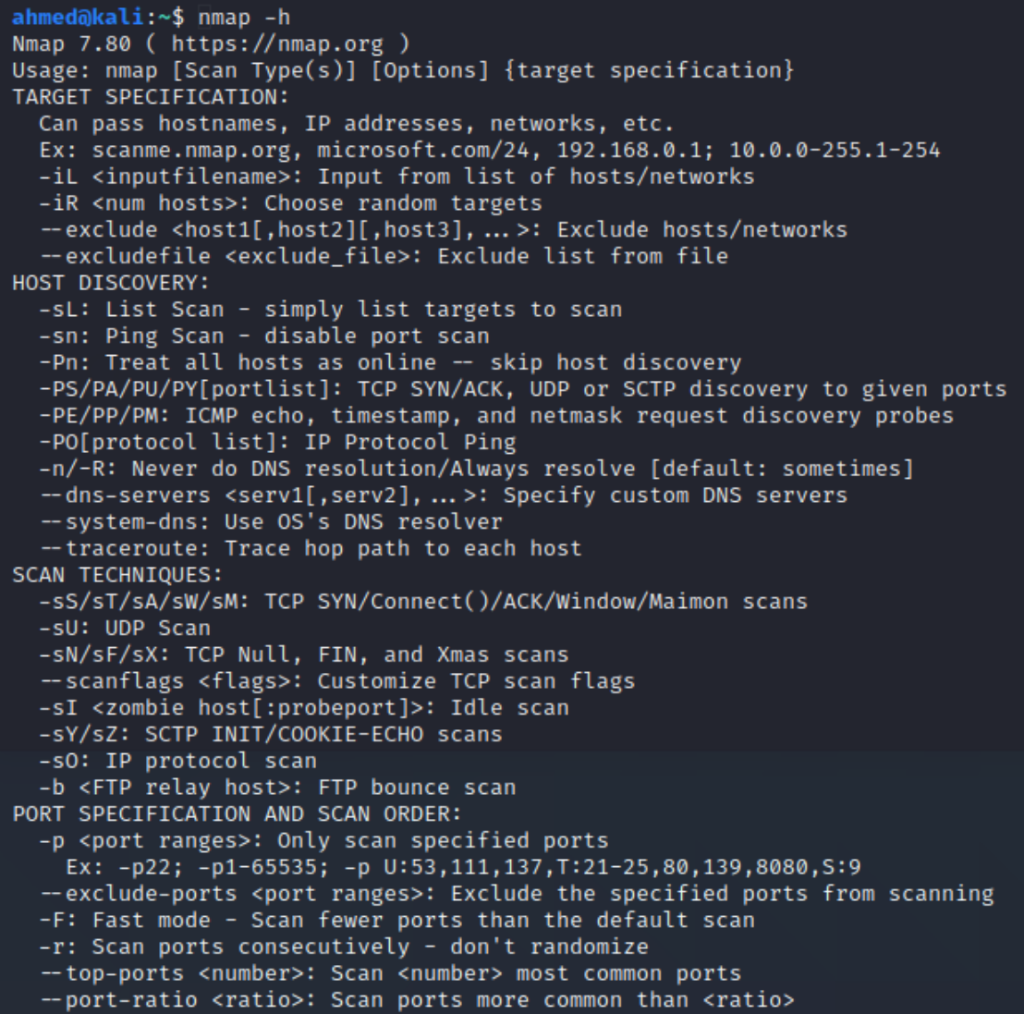
Solved Refer to the screenshots below and answer the

Stealth Port Scanning. Stealth, Decoy or Zombie. By: Larry Brasher
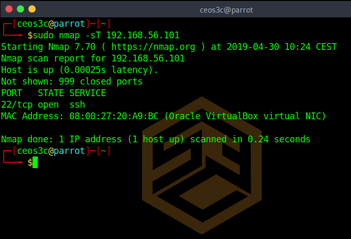
Nmap Tutorial Series 3: Advanced Nmap Commands
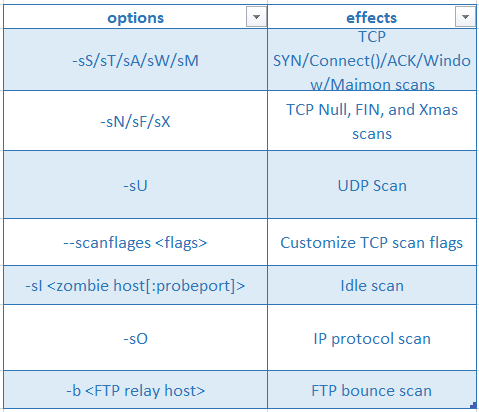
Tools - Nmap
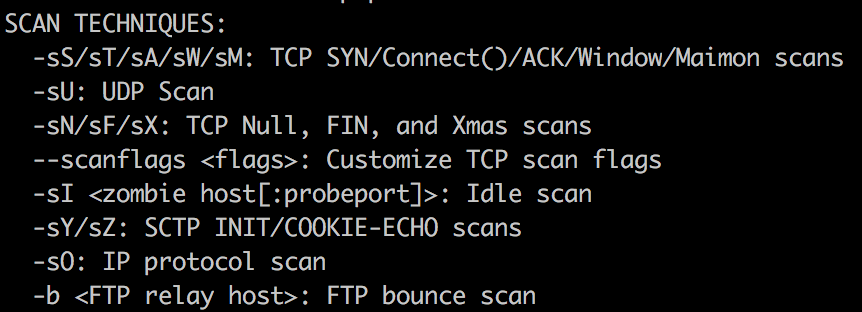
Deep Dive Into Nmap Scan Techniques, by PenTest-duck

Unlocking the Potential of Nmap Scripting, by bob218
Recomendado para você
-
 Show Your Public IP - Restreamer13 maio 2024
Show Your Public IP - Restreamer13 maio 2024 -
![🔴LIVE] How to know my Local PC IP address?](https://i.ytimg.com/vi/HbDJUHhXKhg/maxresdefault.jpg) 🔴LIVE] How to know my Local PC IP address?13 maio 2024
🔴LIVE] How to know my Local PC IP address?13 maio 2024 -
 CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center13 maio 2024
CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center13 maio 2024 -
 How to Find Your Phone's IP Address on Android or iPhone13 maio 2024
How to Find Your Phone's IP Address on Android or iPhone13 maio 2024 -
 Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey13 maio 2024
Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey13 maio 2024 -
 What is port scanning and how does it work?13 maio 2024
What is port scanning and how does it work?13 maio 2024 -
 Malware analysis Malicious activity13 maio 2024
Malware analysis Malicious activity13 maio 2024 -
Ethical Hacking With Net13 maio 2024
-
 Alt using troll awareness meme - Imgflip13 maio 2024
Alt using troll awareness meme - Imgflip13 maio 2024 -
 Hacking Package Pickup13 maio 2024
Hacking Package Pickup13 maio 2024
você pode gostar
-
![Raikou V (GG41/GG70) [Sword & Shield: Crown Zenith] PSA 10](https://www.smokeandmirrorshobby.com/cdn/shop/products/1682130050006_1024x.jpg?v=1682130067) Raikou V (GG41/GG70) [Sword & Shield: Crown Zenith] PSA 1013 maio 2024
Raikou V (GG41/GG70) [Sword & Shield: Crown Zenith] PSA 1013 maio 2024 -
 construction blunders|TikTok Search13 maio 2024
construction blunders|TikTok Search13 maio 2024 -
 Red, Animator vs. Animation Wiki13 maio 2024
Red, Animator vs. Animation Wiki13 maio 2024 -
 Jogo Divertido Para Meninas de 3 4 5 Anos Casinha Completa em Promoção na Americanas13 maio 2024
Jogo Divertido Para Meninas de 3 4 5 Anos Casinha Completa em Promoção na Americanas13 maio 2024 -
 Roblox | CONTA DE BLOX FRUIT LVL MAX COM TODAS13 maio 2024
Roblox | CONTA DE BLOX FRUIT LVL MAX COM TODAS13 maio 2024 -
 Guilherme Briggs pede para deixar dublagem de Chainsaw Man após13 maio 2024
Guilherme Briggs pede para deixar dublagem de Chainsaw Man após13 maio 2024 -
 Noob13 maio 2024
Noob13 maio 2024 -
 List of Minecraft 1.16.5 Shaders13 maio 2024
List of Minecraft 1.16.5 Shaders13 maio 2024 -
Futebol de botão; jogo de botão;13 maio 2024
-
 Senran Kagura Bon Appetit! Limited Run Games #163 PlayStation Vita Brand New!13 maio 2024
Senran Kagura Bon Appetit! Limited Run Games #163 PlayStation Vita Brand New!13 maio 2024

