How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 07 junho 2024
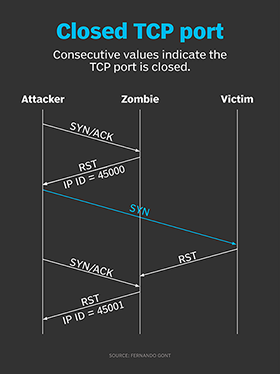
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

PDF) TCP Idle Scanning using network printers

What is a Port Scanner and How Does it Work?
Nmap - Best Network Monitor and Port Scanner Tool - GBHackers
What is a Cyber Attack? Definition and Related FAQs
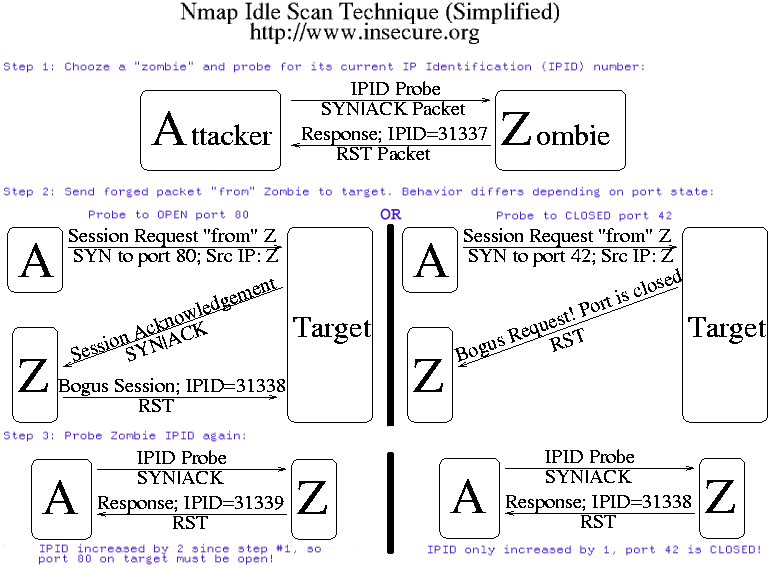
Idle Scanning and related IPID games

What Is an Idle Scan? (with pictures)
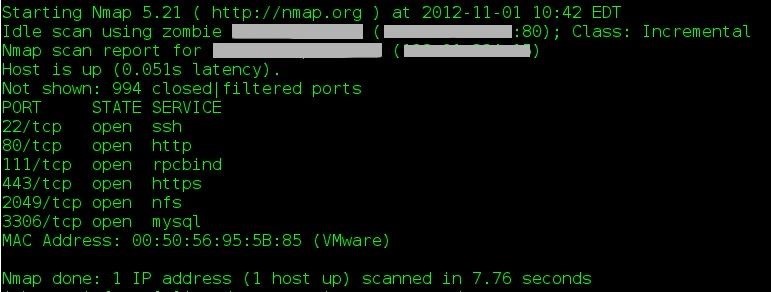
How to Do an Idle Scan with Nmap « Null Byte :: WonderHowTo

№2. Ethical Hacking Labs. Network scanning - HackYourMom

What Is A Port Scan? How To Prevent Port Scan Attacks?
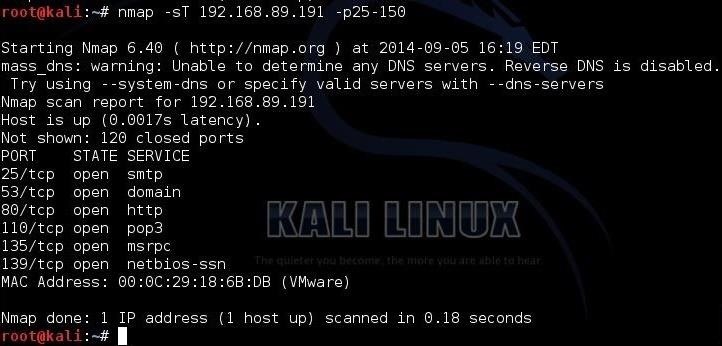
Hack Like a Pro: Advanced Nmap for Reconnaissance « Null Byte :: WonderHowTo
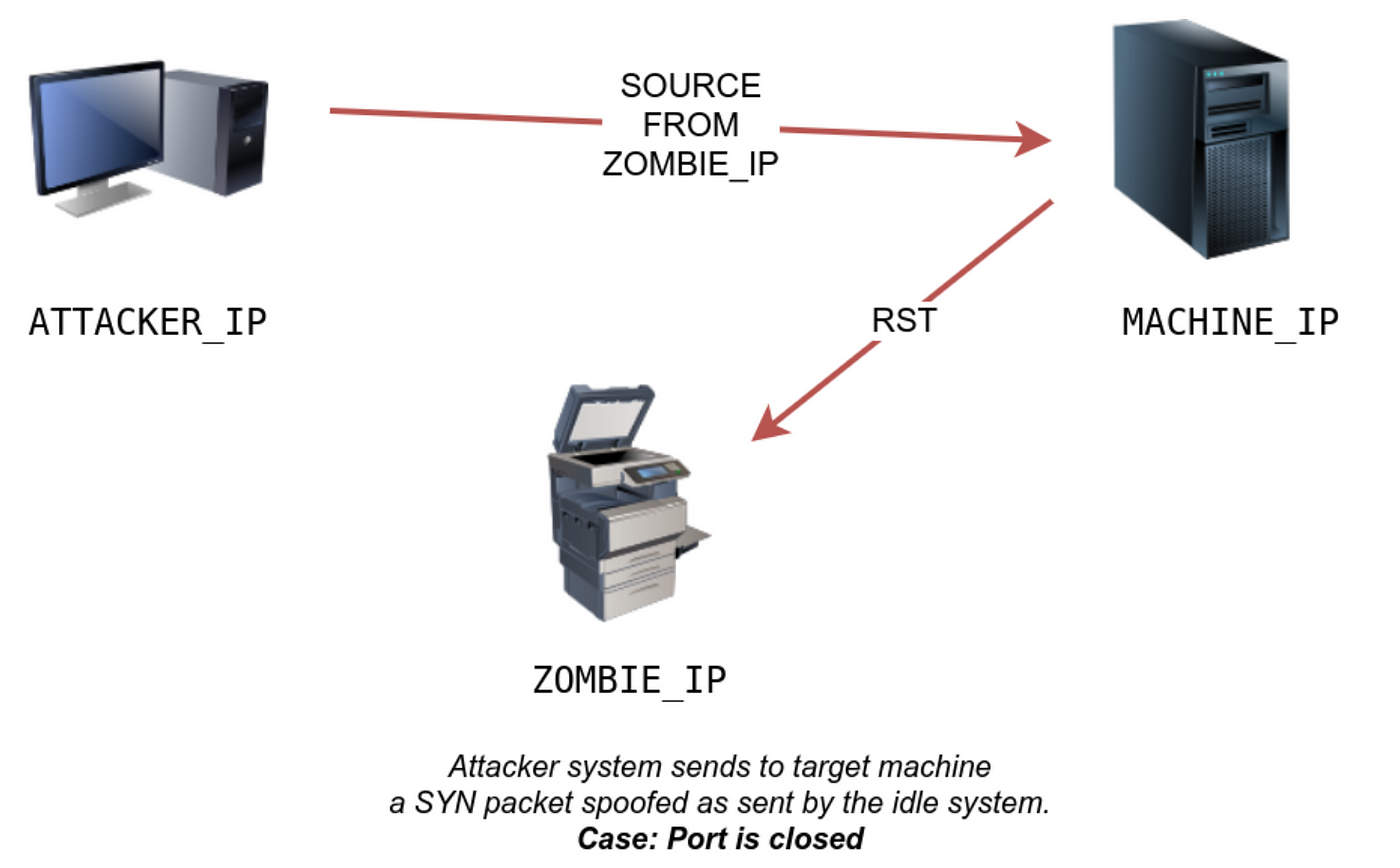
Nmap Advanced Port Scans, TryHackMe (THM), by Aircon
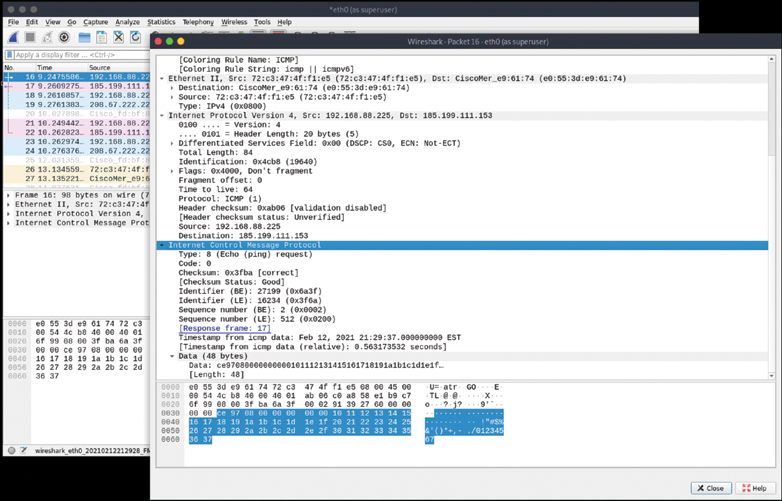
Scanning, Footprinting, Reconnaissance, and Scanning
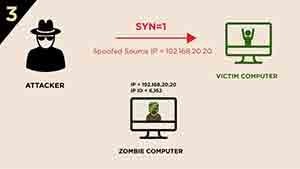
What is Idle Scan? ICterra Information and Communication Technologies
Recomendado para você
-
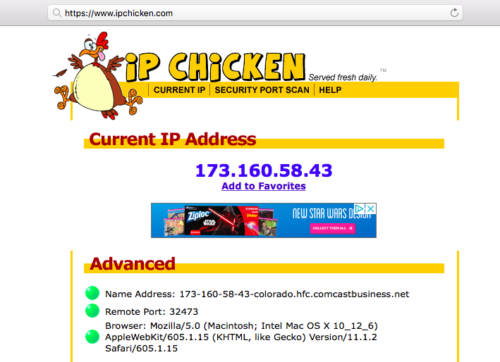 Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201907 junho 2024
Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201907 junho 2024 -
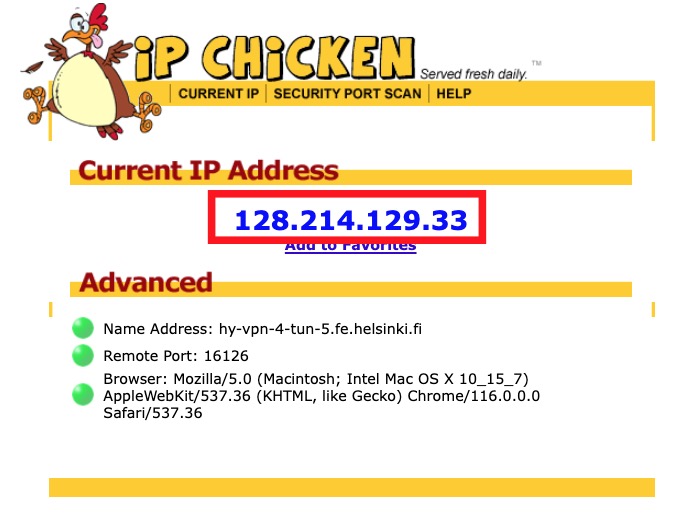 HY-VPN – Checking functionality and errors (Linux)07 junho 2024
HY-VPN – Checking functionality and errors (Linux)07 junho 2024 -
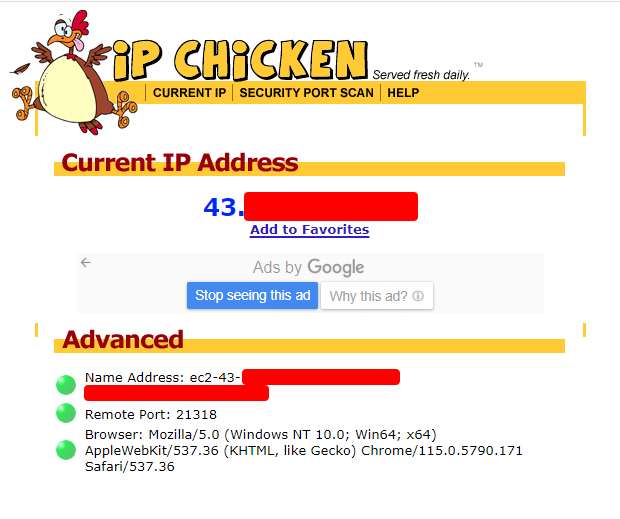 Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K07 junho 2024
Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K07 junho 2024 -
![Question] How to get around VPN blockers?](https://i.gyazo.com/f0c5d0d5b114f0d49954a16dd5112ac7.png) Question] How to get around VPN blockers?07 junho 2024
Question] How to get around VPN blockers?07 junho 2024 -
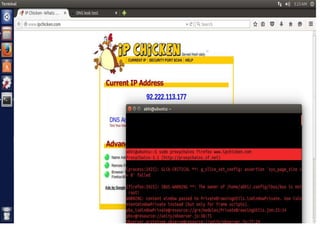 Anonymous Security Scanning and Browsing07 junho 2024
Anonymous Security Scanning and Browsing07 junho 2024 -
 Port Scan in Ethical Hacking - GeeksforGeeks07 junho 2024
Port Scan in Ethical Hacking - GeeksforGeeks07 junho 2024 -
Gogo's T-Mobile sponsored in-flight wifi? Free? On a PC?!07 junho 2024
-
 Alt using troll awareness meme - Imgflip07 junho 2024
Alt using troll awareness meme - Imgflip07 junho 2024 -
 How To Use Tor With Opera Web Browser (With Polipo) For Beginners07 junho 2024
How To Use Tor With Opera Web Browser (With Polipo) For Beginners07 junho 2024 -
 Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download07 junho 2024
Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download07 junho 2024
você pode gostar
-
 White Collar's' Matt Bomer is a terrific actor gay or straight07 junho 2024
White Collar's' Matt Bomer is a terrific actor gay or straight07 junho 2024 -
 Assistir Yu-Gi-Oh! GX Dublado Episodio 126 Online07 junho 2024
Assistir Yu-Gi-Oh! GX Dublado Episodio 126 Online07 junho 2024 -
 MOC Factory Block 89248 Titanfall 2 Ion-class Titan Movies and Games07 junho 2024
MOC Factory Block 89248 Titanfall 2 Ion-class Titan Movies and Games07 junho 2024 -
 Netflix Gift Cards07 junho 2024
Netflix Gift Cards07 junho 2024 -
 Kotobukiya My Little Pony: Twilight Sparkle (Limited Color Variant Edition) Bishoujo, Action Figure Multicolor Anime Model Toys - AliExpress07 junho 2024
Kotobukiya My Little Pony: Twilight Sparkle (Limited Color Variant Edition) Bishoujo, Action Figure Multicolor Anime Model Toys - AliExpress07 junho 2024 -
Xbox now owns Activision Blizzard 🚨 #xbox #microsoft #callofduty #ove07 junho 2024
-
 Legend of Zelda Breath of the Wild gets spooky fan-made DLC for07 junho 2024
Legend of Zelda Breath of the Wild gets spooky fan-made DLC for07 junho 2024 -
 Coup, Image, BoardGameGeek07 junho 2024
Coup, Image, BoardGameGeek07 junho 2024 -
 Jogo De Futebol Pequeno No Gol Colorido Pra Jogar Com Amigos - Alfabay - Cubo Mágico - Quebra Cabeças - A loja de Profissionais e Colecionadores!07 junho 2024
Jogo De Futebol Pequeno No Gol Colorido Pra Jogar Com Amigos - Alfabay - Cubo Mágico - Quebra Cabeças - A loja de Profissionais e Colecionadores!07 junho 2024 -
 Unveiling the Humorous World of Animan Studios Memes » NetworkUstad07 junho 2024
Unveiling the Humorous World of Animan Studios Memes » NetworkUstad07 junho 2024

