6 confirmed signs of key logger infections and their prevention on computer and mobile!
Por um escritor misterioso
Last updated 01 junho 2024

It is crucial to know about keyloggers as they play a significant role in the world of cybersecurity. Often, computers and smartphones show several signs when they get infected with a keylogger.

What are Keyloggers and How Can You Protect Yourself?

5 Ways to Protect Yourself Against Keyloggers

How to tell if you've been hacked (Plus what you can do about it)

Cyber security experts reveal 10 worrying signs that hackers are spying on your phone - Irish Mirror Online
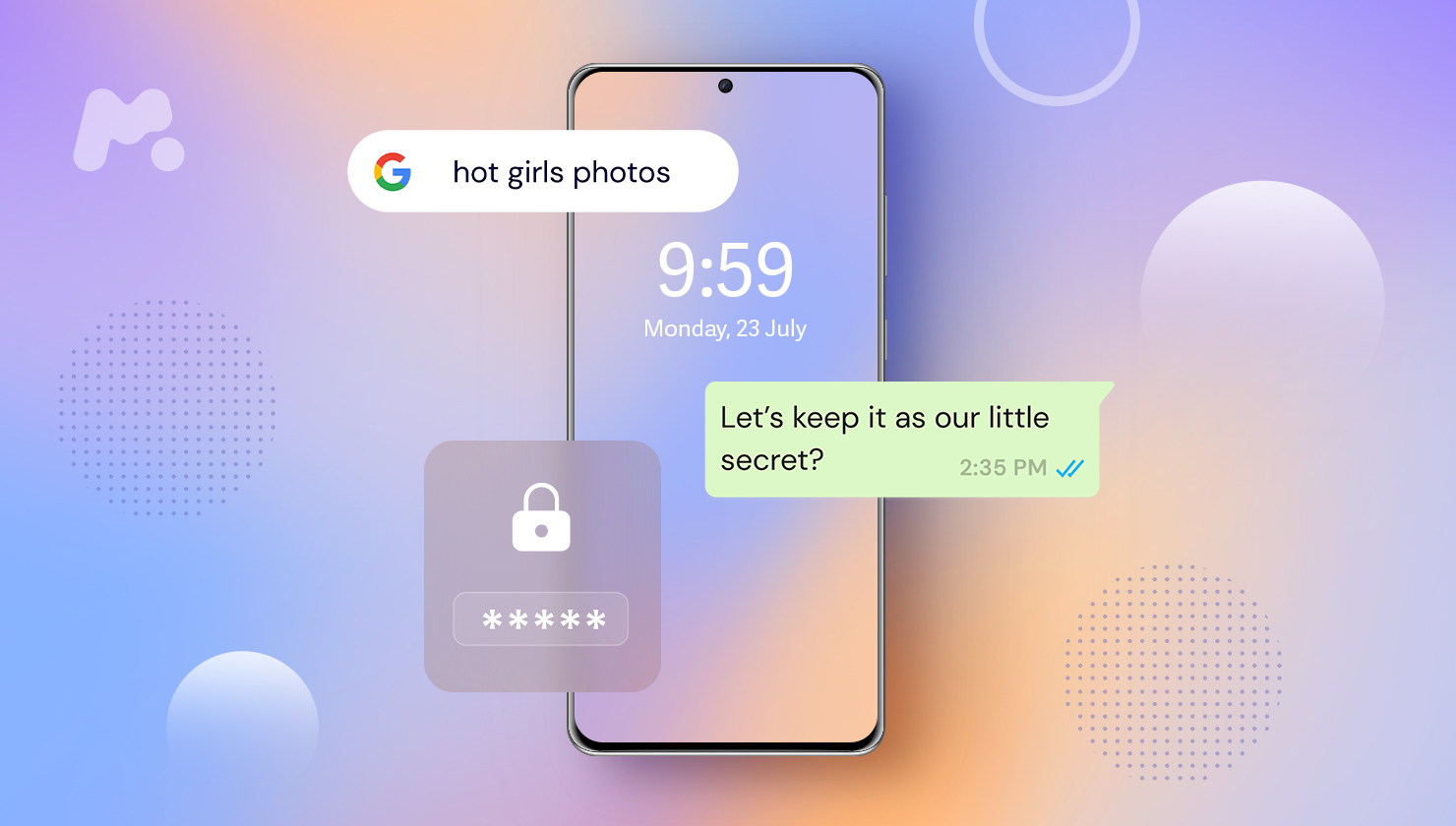
How to Detect a Keylogger? 5 Signs That Your Android Phone Is Monitored

What are Keyloggers and How Can You Protect Yourself?

What is a Keylogger? Keystroke Logging & How to Prevent It

Malware and best practices for malware removal

6 confirmed signs of key logger infections and their prevention on computer and mobile!

Keylogger Infection: Signs, Risks, and Prevention - ITSecurityWire
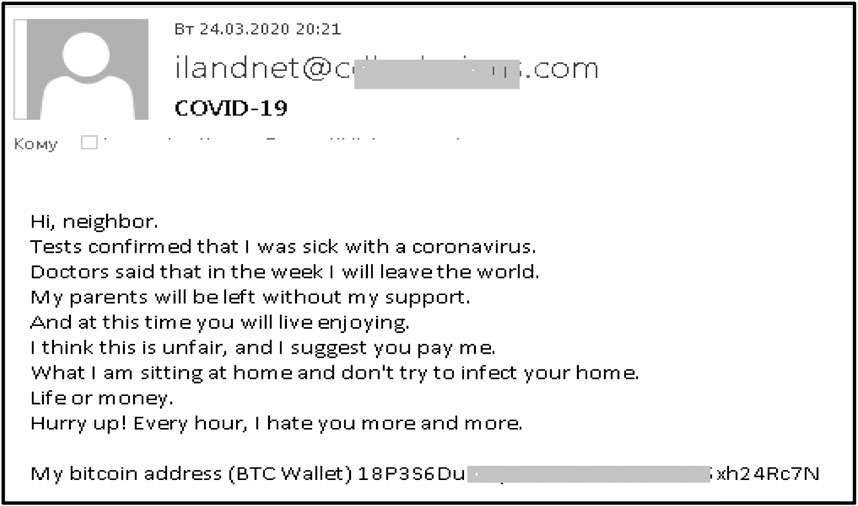
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy
Recomendado para você
-
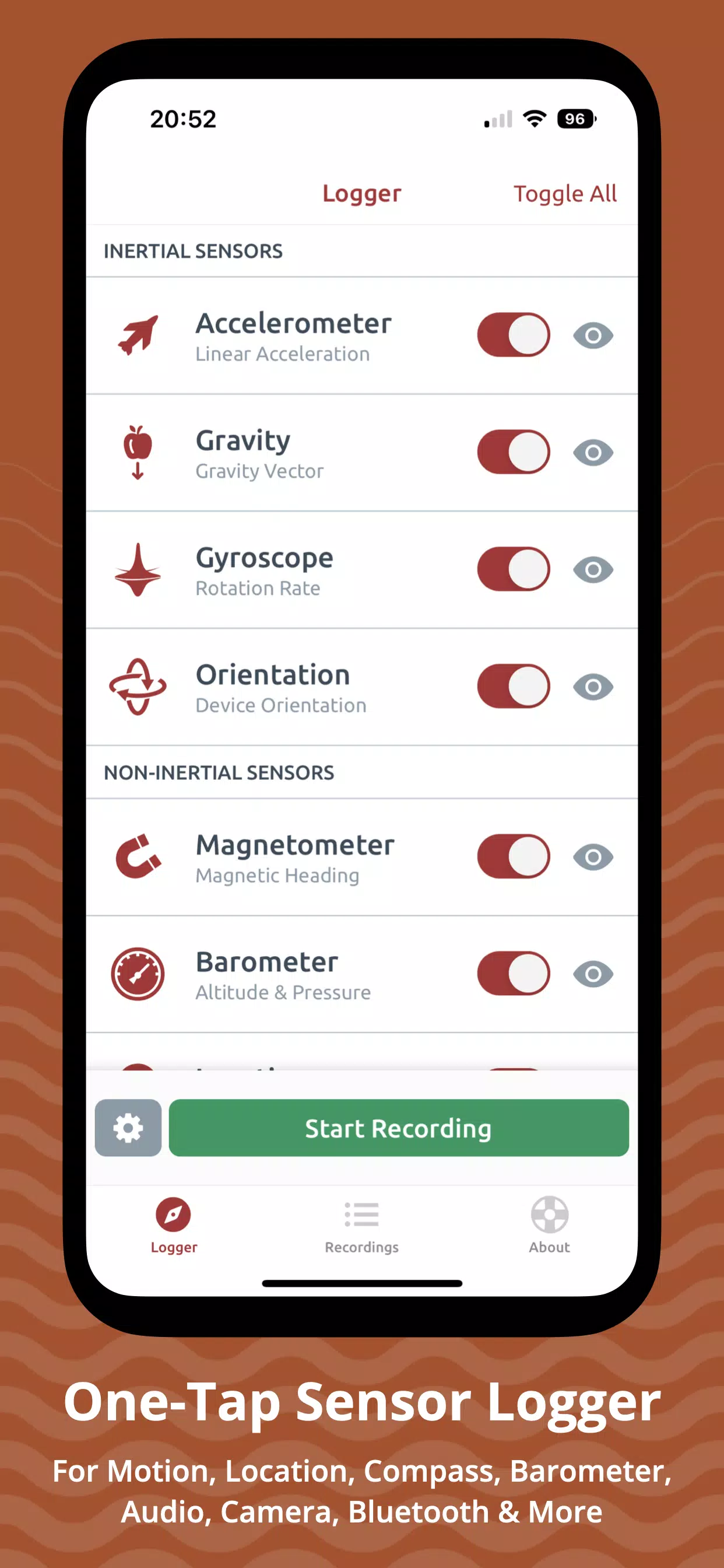 Sensor Logger APK for Android Download01 junho 2024
Sensor Logger APK for Android Download01 junho 2024 -
 Kapture KPT-592 FHD Front & Rear Dash Camera with 3.2 Screen GPS Logger - JB Hi-Fi01 junho 2024
Kapture KPT-592 FHD Front & Rear Dash Camera with 3.2 Screen GPS Logger - JB Hi-Fi01 junho 2024 -
 REVIEWING Audio LOGGER Script Edges Audio Logger01 junho 2024
REVIEWING Audio LOGGER Script Edges Audio Logger01 junho 2024 -
 Shell Script Audio Logger01 junho 2024
Shell Script Audio Logger01 junho 2024 -
 You can still exploit on chromeos with ARCVM & android executor : r/robloxhackers01 junho 2024
You can still exploit on chromeos with ARCVM & android executor : r/robloxhackers01 junho 2024 -
 ROBLOX PRIVATE/PUBLIC AUDIO DOWNLOADER FREE GUI – WINDOWS & MACOS SUPPORT –01 junho 2024
ROBLOX PRIVATE/PUBLIC AUDIO DOWNLOADER FREE GUI – WINDOWS & MACOS SUPPORT –01 junho 2024 -
roblox-script · GitHub Topics · GitHub01 junho 2024
-
 Roblox acquires Byfron anticheat : r/ROBLOXExploiting01 junho 2024
Roblox acquires Byfron anticheat : r/ROBLOXExploiting01 junho 2024 -
 Roblox exploiting Showcasing dot_mp4's anti-logger gui (v4)01 junho 2024
Roblox exploiting Showcasing dot_mp4's anti-logger gui (v4)01 junho 2024 -
 Audio Spectrum Analyzer - OscilloMeter - Download01 junho 2024
Audio Spectrum Analyzer - OscilloMeter - Download01 junho 2024
você pode gostar
-
 King of the Hill The Complete Series DVD 37-Disc Season 1-1301 junho 2024
King of the Hill The Complete Series DVD 37-Disc Season 1-1301 junho 2024 -
 Reaper sans Undertale, Undertale drawings, Undertale au01 junho 2024
Reaper sans Undertale, Undertale drawings, Undertale au01 junho 2024 -
 The best Netflix TV shows: The only Netflix series you need to be01 junho 2024
The best Netflix TV shows: The only Netflix series you need to be01 junho 2024 -
 Download Caption: Anime Enthusiast's Delight - Portrait Of Miyamura Izumi Wallpaper01 junho 2024
Download Caption: Anime Enthusiast's Delight - Portrait Of Miyamura Izumi Wallpaper01 junho 2024 -
 Create a Astd Tier List - TierMaker01 junho 2024
Create a Astd Tier List - TierMaker01 junho 2024 -
 Fútbol uruguayo. Previo al clásico Argentina-Uruguay se juega la Fecha 10 del Clausura01 junho 2024
Fútbol uruguayo. Previo al clásico Argentina-Uruguay se juega la Fecha 10 del Clausura01 junho 2024 -
Unidade - 01 - Dança de Salão 1, PDF, Dança de salão01 junho 2024
-
letra da musica menina ta ficando muito tarde de luisa sonza|TikTok Search01 junho 2024
-
 4 Pics 1 Logo Quiz : what's the brand 100 guess word by YOUNG MOO LEE01 junho 2024
4 Pics 1 Logo Quiz : what's the brand 100 guess word by YOUNG MOO LEE01 junho 2024 -
Resurfacing Retinol Facial Serum for Acne Prone Skin - CeraVe01 junho 2024